In today’s digital-first world, IT security is no longer optional—it is essential. Every organization, regardless of size or industry, faces growing cybersecurity risks such as data breaches, ransomware attacks, phishing scams, and unauthorized access. To safeguard systems, protect customer trust, and maintain compliance, companies must implement strong security practices.
One of the most effective tools to ensure these practices remain consistent is an IT Security Review Checklist in Excel. A checklist provides structure, accountability, and visibility, making it easier for IT teams and business leaders to stay proactive in protecting sensitive data.
Click to Purchases IT Security Review Checklist in Excel
In this article, we will explore the concept of an IT Security Review Checklist, its structure in Excel, its benefits, best practices for usage, and frequently asked questions. By the end, you will understand not only how this checklist works but also how it can strengthen your organization’s security posture.
What Is an IT Security Review Checklist?
An IT Security Review Checklist is a structured list of security-related tasks, checks, and controls that organizations use to evaluate and maintain the effectiveness of their IT security policies.
Instead of relying on memory or scattered notes, this checklist ensures that every critical step—such as access control, software updates, network monitoring, or backup verification—gets recorded, assigned, and tracked.
By maintaining this checklist in Excel, businesses gain a simple yet powerful way to document responsibilities, deadlines, and status updates. The flexibility of Excel also allows teams to customize the checklist to their unique security needs.
Key Features of the IT Security Review Checklist Template in Excel
This ready-to-use Excel template is designed with efficiency and clarity in mind. It includes two main worksheets:
IT Security Review Checklist Sheet
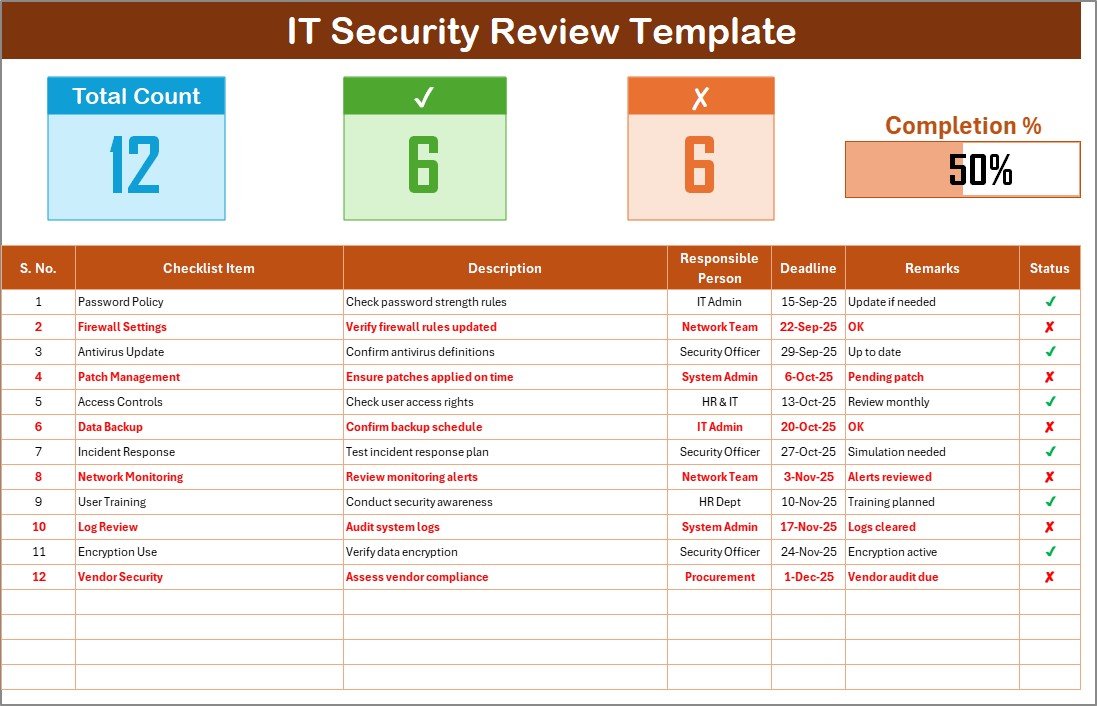
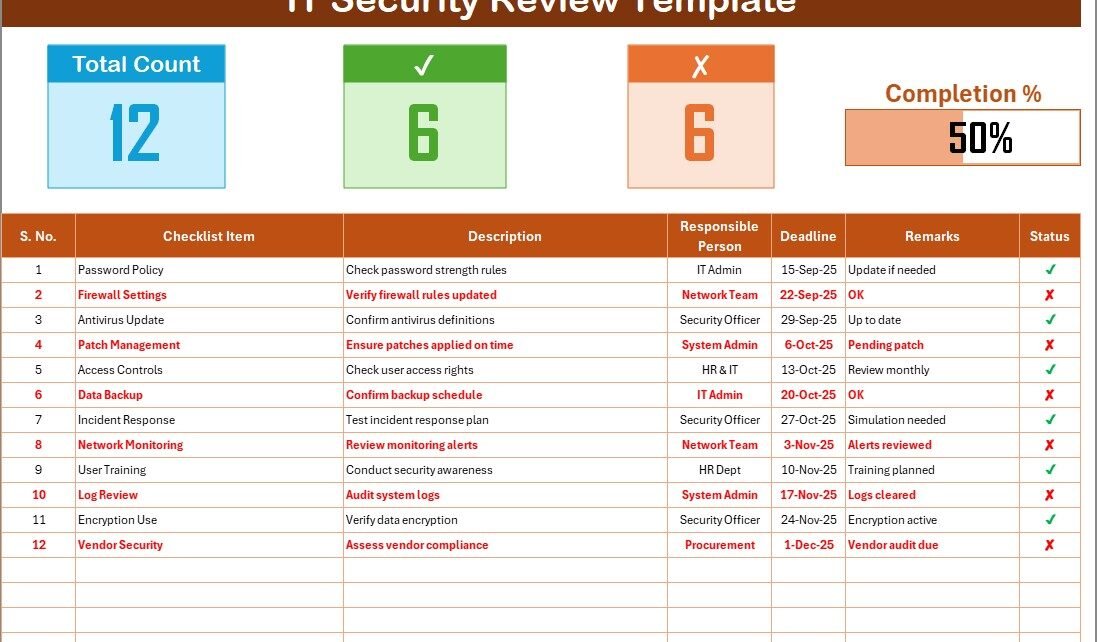
This is the main sheet where you record and manage security tasks.
Top Section
Displays summary information:
- Total Count of checklist items
- Checked count
- Crossed count
- Progress bar showing completion percentage
Checklist Table
The table includes the following columns:
- Serial No. – Sequential number of the checklist item
- Checklist Item – The name of the security task
- Description – Brief details of the task
- Responsible Person – The team member accountable
- Deadline – The due date for task completion
- Remarks – Additional notes or observations
- Status – Marked as ✔ (completed) or ✘ (not completed)
This sheet provides a structured, at-a-glance view of your IT security tasks.
List Sheet

This sheet captures the unique list of responsible persons. It powers the drop-down list in the main checklist table, ensuring that task assignments remain consistent and easy to manage.
Why Use Excel for IT Security Review?
Excel may not be the first tool that comes to mind for IT security tracking, but it offers unique advantages:
-
Simplicity – Most teams are already familiar with Excel.
-
Customization – Modify the checklist to suit your organization’s unique needs.
-
Accessibility – Easily share with stakeholders and team members.
-
Tracking – Built-in formulas, conditional formatting, and progress bars provide real-time visibility.
-
Accountability – Assign responsibilities with clear deadlines and updates.
Excel remains a universal platform that bridges technical and non-technical teams, making it a perfect choice for checklist-based IT security reviews.
Click to Purchases IT Security Review Checklist in Excel
How to Use the IT Security Review Checklist
Here’s a step-by-step guide to using the Excel template effectively:
Set Up the Checklist
- Open the template.
- Review the pre-filled structure and customize it to match your security framework.
List Security Tasks
- Add tasks such as “Update antivirus software,” “Review firewall settings,” or “Test disaster recovery plan.”
Assign Responsibilities
- Use the drop-down menu to assign each task to the right person.
Define Deadlines
- Enter due dates to ensure tasks are completed on time.
Monitor Progress
- Update the status column as tasks get completed.
- Track completion percentage with the progress bar.
Review and Audit
- Use the checklist during regular IT audits.
- Record remarks for each completed or pending task.
This systematic approach ensures that nothing falls through the cracks.
Advantages of IT Security Review Checklist in Excel
Using an Excel-based checklist offers multiple benefits to businesses:
✅ Improved Accountability – Every task has a responsible person and deadline.
✅ Increased Efficiency – Teams can work faster with clear instructions.
✅ Enhanced Compliance – Demonstrates adherence to regulations such as GDPR, HIPAA, or ISO standards.
✅ Reduced Risks – Prevents oversight of critical tasks like patching or backups.
✅ Easy Collaboration – Share the file with IT teams, management, and auditors.
✅ Visual Tracking – Progress bars and counts provide a clear overview.
This makes the checklist not only a tool for daily operations but also a valuable resource during audits and compliance reviews.
Best Practices for the IT Security Review Checklist
To maximize the effectiveness of your checklist, follow these best practices:
-
Keep It Updated
Regularly update tasks based on evolving threats. -
Prioritize Critical Tasks
Highlight tasks such as access reviews and patch management. -
Use Conditional Formatting
Apply color coding for overdue or pending tasks. -
Automate Where Possible
Add formulas for progress tracking and alerts. -
Schedule Regular Reviews
Conduct weekly or monthly reviews to stay on top of security. -
Integrate with Policies
Align the checklist with your organization’s IT security policies. -
Train Team Members
Ensure all responsible persons know how to update the checklist.
By following these practices, you can transform a simple checklist into a powerful security management tool.
Common Tasks to Include in an IT Security Review Checklist
Here are some examples of tasks you might include:
-
Verify antivirus and anti-malware updates
-
Review firewall configurations
-
Audit user access permissions
-
Check data backup schedules
-
Test disaster recovery plan
-
Apply security patches and updates
-
Monitor login attempts and system logs
-
Verify encryption settings
-
Update incident response plan
-
Conduct phishing awareness training
These tasks ensure that your IT infrastructure remains secure, resilient, and compliant.
Challenges of IT Security Reviews
While checklists make the process easier, organizations may still face challenges such as:
-
Rapidly evolving threats – Cyber risks change faster than policies.
-
Limited resources – Small teams may struggle to cover every task.
-
Human error – Manual checklists rely on accurate updates.
-
Resistance to adoption – Team members may forget or avoid updating the file.
Acknowledging these challenges helps you design better workflows and adopt additional tools like automated monitoring systems.
Opportunities for Improvement in IT Security Checklists
Even a good checklist can be made better. Here are opportunities to improve:
-
Integrate with cloud platforms like SharePoint or Google Drive for real-time collaboration.
-
Add advanced tracking features such as pivot tables for reporting.
-
Include severity levels (High, Medium, Low) for prioritization.
-
Combine with dashboards to visualize performance trends.
-
Link to external policies or SOPs for quick reference.
These enhancements turn the checklist into a more dynamic and strategic asset.
Conclusion
IT security is a journey, not a destination. With rising cyber threats, organizations must take a proactive approach to safeguard their systems, data, and people.
An IT Security Review Checklist in Excel offers a simple yet highly effective way to track, assign, and review security practices. Its structured approach ensures accountability, compliance, and improved protection against risks.
By customizing and maintaining this checklist, your organization can build a stronger security culture while simplifying audits and compliance reporting.
Frequently Asked Questions (FAQs)
1. What is an IT Security Review Checklist in Excel?
It is a structured Excel-based tool that helps organizations track, assign, and monitor IT security tasks such as access reviews, patch updates, and backups.
2. Why should I use Excel for IT security reviews?
Excel provides flexibility, ease of use, and wide accessibility, making it a cost-effective choice for managing security checklists.
3. Can small businesses benefit from this checklist?
Yes, small businesses can benefit the most because it provides structure and accountability without needing expensive software.
4. How often should I update the checklist?
Review and update the checklist at least monthly. For critical systems, weekly updates are recommended.
5. Can this checklist help with compliance audits?
Yes, it creates a documented record of completed tasks, which auditors can use as proof of compliance.
6. Can I customize the template for my company?
Absolutely. You can add, remove, or adjust checklist items based on your organization’s security policies and industry standards.
Visit our YouTube channel to learn step-by-step video tutorials
Click to Purchases IT Security Review Checklist in Excel