In today’s fast-paced digital world, cybersecurity is more important than ever. With the rise in cyber threats, organizations must prioritize security measures to protect sensitive data, infrastructure, and reputation. One of the most effective ways to manage and track cybersecurity tasks is by using a Cybersecurity To-Do List Checklist. This Excel template is designed to streamline your cybersecurity efforts, helping you stay on top of essential security tasks and reduce the risk of potential breaches.
In this article, we’ll explore how to create and use a Cybersecurity To-Do List Checklist in Excel, the advantages of using such a checklist, and some best practices for maintaining an effective cybersecurity program.
Click to Purchases Cybersecurity To-Do List Checklist in Excel
Key Features of the Cybersecurity To-Do List Checklist Template
The Cybersecurity To-Do List Checklist in Excel is a ready-to-use template that comes with two essential worksheets:
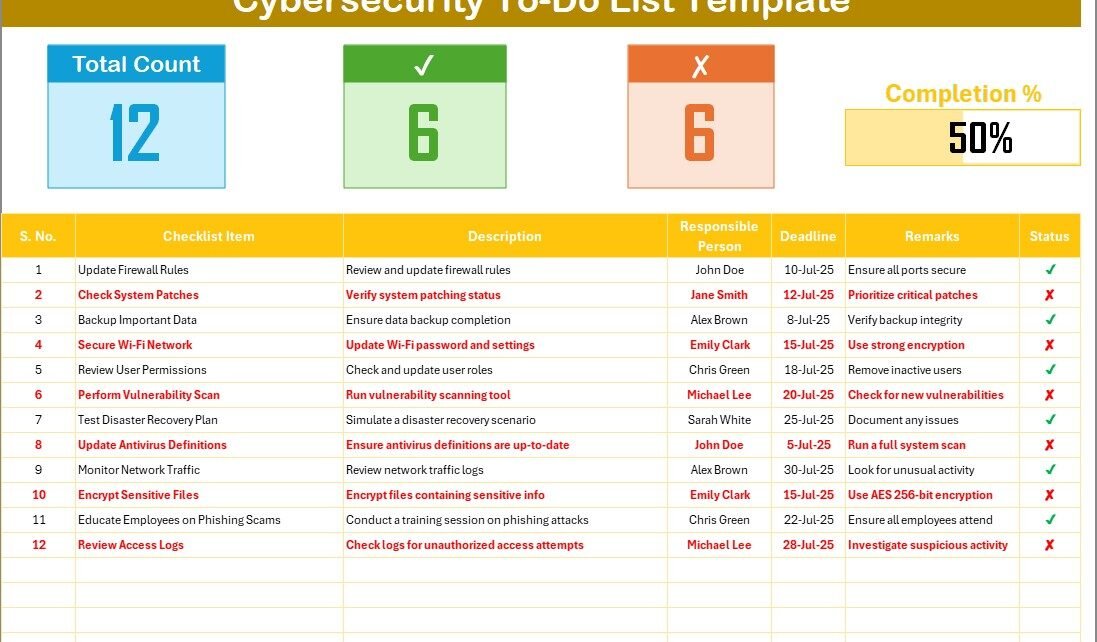
Cybersecurity To-Do List Checklist Sheet

This is the main worksheet where you will manage all your cybersecurity tasks. The sheet provides an organized way to track progress, assign responsibilities, and set deadlines.
Top Section
In the top section of the sheet, you’ll find the following key features:
-
Total Count: The total number of items on your checklist.
-
Checked Count: A tally of completed tasks.
-
Crossed Count: A record of the tasks that have been marked as irrelevant or cancelled.
-
Progress Bar: A visual progress bar that shows the percentage of completed tasks, helping you quickly assess your overall progress.
Checklist Table
This table is where the core action happens. You can customize the table to fit your organization’s specific cybersecurity needs. The table includes the following columns:
-
Serial No.: The number assigned to each task for easy reference.
-
Checklist Item: A short description of the task that needs to be completed.
-
Description: A more detailed explanation of the task.
-
Responsible Person: The individual or team assigned to the task.
-
Deadline: The due date for completing the task.
-
Remarks: Any additional notes or comments regarding the task.
-
Status: This column allows you to mark the task as completed (✔) or not completed (✘), providing a quick overview of where each task stands.
List Sheet Tab
The List Sheet is a separate tab where you can maintain a unique list of all responsible individuals or teams. This list is used to create a drop-down menu for the “Responsible Person” column in the main checklist, ensuring consistency and reducing the chances of human error.
Advantages of Using a Cybersecurity To-Do List Checklist in Excel
Managing cybersecurity tasks without a structured approach can lead to missed deadlines, overlooked issues, and increased vulnerability. Here’s why using a Cybersecurity To-Do List Checklist in Excel is essential:
1. Organization and Clarity
A structured checklist helps you break down complex cybersecurity tasks into manageable, clear steps. By organizing your security tasks in a single, easy-to-use template, you’ll know exactly what needs to be done, who is responsible, and when it needs to be completed.
2. Improved Task Tracking
With features like the Total Count, Checked Count, and Progress Bar, you can easily track your progress. This visual tracking ensures that all tasks are completed on time and nothing is left undone.
3. Better Collaboration
Assigning tasks to specific individuals or teams promotes collaboration. The Responsible Person field ensures that everyone knows their responsibilities, while the List Sheet provides a centralized database for all assigned personnel.
4. Customizable for Your Needs
The template is highly customizable. Whether you are a small business or a large enterprise, you can tailor the checklist to your organization’s unique cybersecurity needs. Add, remove, or modify columns and tasks to suit your requirements.
5. Increased Accountability
By assigning a Responsible Person to each task and setting deadlines, the checklist holds individuals accountable for their actions. This accountability ensures that everyone takes ownership of their tasks, ultimately strengthening the security posture of your organization.
Best Practices for Using a Cybersecurity To-Do List Checklist in Excel
To ensure that your Cybersecurity To-Do List Checklist is as effective as possible, follow these best practices:
1. Regularly Update the Checklist
Cybersecurity is an ever-evolving field, and tasks may change over time. Regularly update your checklist to reflect new tasks, updated priorities, and changes in the cybersecurity landscape. Make sure your team has access to the latest version.
2. Assign Clear Deadlines
Set realistic deadlines for each task. Be sure to consider the urgency of each task, and assign time frames that are achievable. This will help your team stay focused and organized, reducing the risk of delays or missed deadlines.
3. Use the Progress Bar Effectively
The progress bar is a powerful tool for visualizing your progress. Make sure you update the checklist regularly to ensure the progress bar reflects the true status of each task. This will help you quickly assess whether you’re on track or need to accelerate your efforts.
4. Prioritize Tasks
Cybersecurity tasks often vary in urgency. Prioritize tasks based on their importance and potential impact. High-priority tasks should be marked and completed first, while lower-priority tasks can be addressed later.
5. Communicate Clearly with Your Team
Ensure that everyone involved in cybersecurity tasks understands the checklist, the deadlines, and their responsibilities. Clear communication is key to staying organized and maintaining an efficient workflow.
6. Backup Your Data
Since the checklist will likely be shared and updated by multiple team members, it’s important to regularly back up your data. Make sure your Excel file is stored in a secure location with version control to avoid losing important information.
Conclusion
The Cybersecurity To-Do List Checklist in Excel is an indispensable tool for managing and tracking cybersecurity tasks. By organizing tasks, assigning responsibilities, and monitoring progress, this template helps ensure that your organization remains secure and proactive in the face of ever-evolving cyber threats. Whether you are working individually or as part of a team, this checklist will streamline your cybersecurity efforts and improve accountability and efficiency.
Frequently Asked Questions (FAQs)
What is the purpose of a Cybersecurity To-Do List Checklist?
A Cybersecurity To-Do List Checklist helps organizations stay on top of their cybersecurity tasks. It ensures that all critical tasks are completed on time, assigned to the right individuals, and tracked for progress.
How do I use the Cybersecurity To-Do List Template in Excel?
The template is simple to use. Add your tasks to the checklist, assign them to responsible individuals, set deadlines, and update the status column as tasks are completed. Use the Progress Bar and Total Count sections to track your progress.
Can I customize the Cybersecurity To-Do List Checklist?
Yes! The checklist is fully customizable. You can add or remove columns, tasks, and deadlines as needed to fit your organization’s specific cybersecurity needs.
How does the Responsible Person list work?
The Responsible Person field is linked to a drop-down list that you can create in the List Sheet tab. This ensures consistency when assigning tasks and avoids errors in the checklist.
How often should I update the checklist?
You should update the checklist regularly to reflect new cybersecurity tasks, changes in priorities, and updates in your organization’s security protocols. It is also important to update the checklist when tasks are completed or deadlines are adjusted.
Visit our YouTube channel to learn step-by-step video tutorials