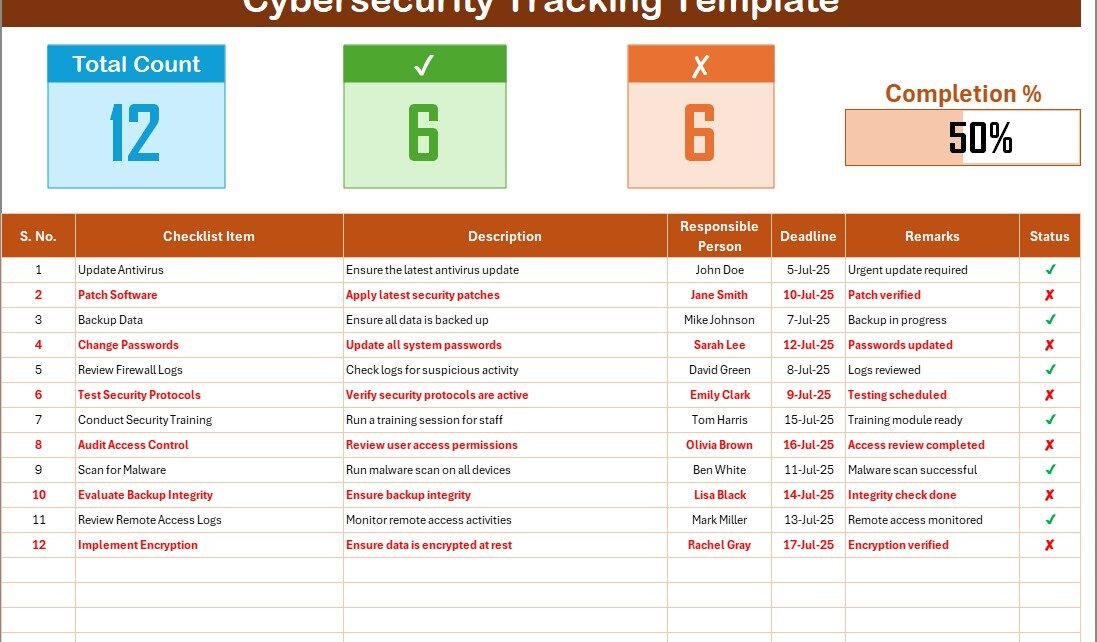
In today’s digital world, cybersecurity has become one of the most pressing concerns for organizations. With increasing threats and sophisticated attacks, businesses need to stay ahead in securing their data and operations. One of the most effective ways to ensure robust cybersecurity practices is through a well-organized checklist. A Cybersecurity Tracking Checklist in Excel is a simple yet powerful tool to track and monitor security measures, ensuring that no critical task is overlooked.
In this article, we will explore how you can leverage a Cybersecurity Tracking Checklist in Excel to manage your security tasks effectively. We will discuss its key features, advantages, best practices, and more, providing you with a detailed guide on how to implement it in your organization.
Click to Purchases Cybersecurity Tracking Checklist in Excel
What is a Cybersecurity Tracking Checklist in Excel?
A Cybersecurity Tracking Checklist is a tool designed to help organizations manage their cybersecurity efforts. It tracks tasks and responsibilities related to cybersecurity activities, helping you stay on top of critical actions such as software updates, system audits, and employee training.
An Excel-based Cybersecurity Tracking Checklist brings several advantages to the table, including ease of use, accessibility, and the ability to customize and update as your security needs evolve. It allows you to monitor key activities, assign tasks, and track their completion in one place.
Key Features of a Cybersecurity Tracking Checklist in Excel
An effective Cybersecurity Tracking Checklist contains the following core features:
Cybersecurity Tracking Checklist Sheet
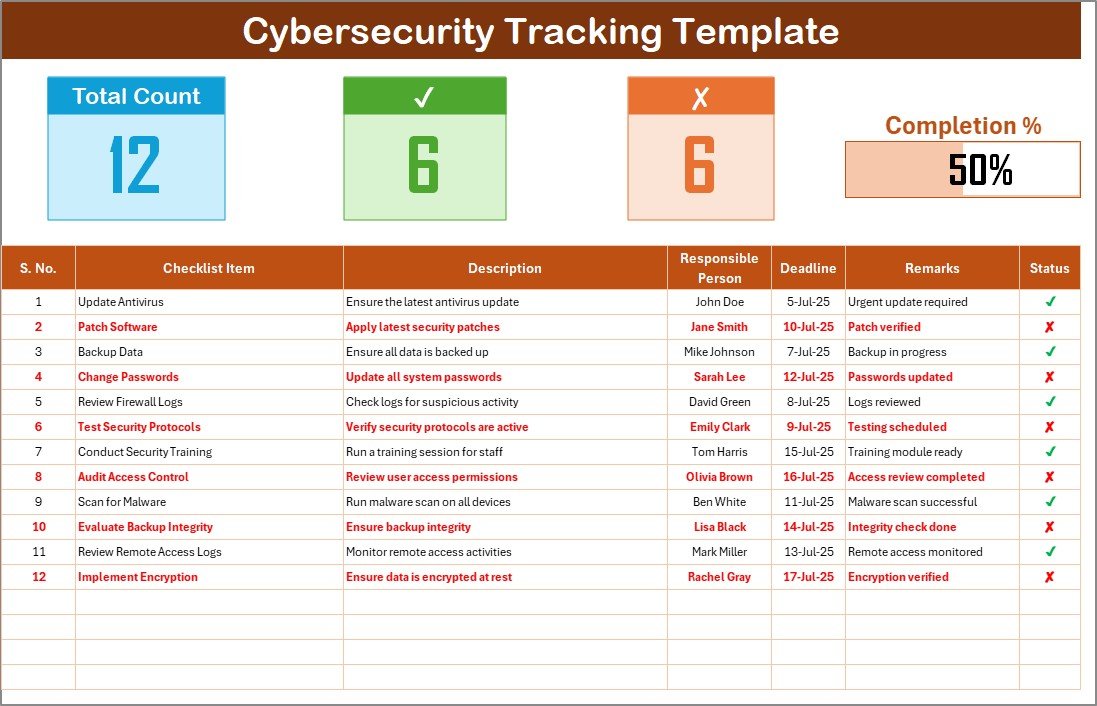
This is the primary worksheet where all the cybersecurity tracking tasks are captured. It includes:
-
Total Count: Displays the total number of checklist items.
-
Checked Count: Shows how many tasks have been completed.
-
Crossed Count: Indicates the number of tasks that have been marked as irrelevant or not needed.
-
Progress Bar: Visualizes the percentage of completed tasks, giving a quick overview of your cybersecurity efforts.
Checklist Table
The checklist table is the heart of the tracking template. It allows users to monitor cybersecurity tasks and mark their completion status. The table consists of the following columns:
-
Serial No.: A unique identifier for each task.
-
Checklist Item: The specific cybersecurity task or requirement.
-
Description: A brief explanation of the task.
-
Responsible Person: The individual or team responsible for the task.
-
Deadline: The due date for completing the task.
-
Remarks: Any additional notes related to the task.
-
Status: This column allows users to mark each task as ✔ (completed) or ✘ (not completed).
List Sheet Tab

This sheet is used to maintain a unique list of Responsible Persons, which is later used to create a drop-down list in the Checklist Table. This helps streamline task assignment and ensures clarity on who is responsible for each task.
Advantages of Using a Cybersecurity Tracking Checklist in Excel
Utilizing a Cybersecurity Tracking Checklist in Excel offers numerous benefits that can significantly enhance your cybersecurity management efforts:
1. Improved Organization
A well-structured checklist allows you to organize your cybersecurity tasks efficiently. You can prioritize tasks based on deadlines, track completion, and quickly identify any overdue activities. This reduces the chances of missing critical tasks, improving overall security.
2. Simplified Task Assignment
With a drop-down list of responsible persons, you can easily assign tasks to the appropriate team members. This ensures that everyone knows their responsibilities and that no tasks are left unassigned.
3. Real-Time Monitoring
The Progress Bar feature helps you monitor the status of your cybersecurity efforts in real time. You can instantly see how much work has been completed and how much is still pending, making it easier to manage resources and deadlines.
4. Increased Accountability
By specifying deadlines and responsible individuals, the checklist encourages accountability. Team members are more likely to complete their assigned tasks on time, knowing they are being tracked.
5. Easy Customization
Since the template is in Excel, it can be easily customized to fit your organization’s specific needs. You can add or remove checklist items, adjust columns, and modify the structure as necessary.
6. Cost-Effective
Using an Excel-based checklist eliminates the need for costly cybersecurity management software. You get a powerful tool at no extra cost, leveraging the existing capabilities of Microsoft Excel.
Best Practices for Cybersecurity Tracking Checklist in Excel
To maximize the effectiveness of your Cybersecurity Tracking Checklist, it’s important to follow best practices. Below are some essential guidelines to ensure you get the most out of this tool:
1. Regularly Update the Checklist
Cybersecurity is a constantly evolving field. New threats emerge every day, and tasks need to be updated to address these threats. Make it a habit to review and update the checklist regularly to ensure it remains relevant.
2. Assign Clear Deadlines
Setting deadlines for each task is critical for staying on track. Clearly defined timelines help ensure that tasks are completed on schedule and allow you to monitor progress efficiently.
3. Use Conditional Formatting for Better Visibility
To improve the readability and usability of your checklist, use conditional formatting in Excel. You can set rules to highlight overdue tasks or those that are approaching their deadline. This will help you stay proactive and address issues before they become critical.
4. Include Regular Security Audits
Incorporate regular security audits into your checklist. This includes reviewing systems, software, and security policies to ensure they comply with industry standards and regulations. Regular audits will help you identify vulnerabilities and address them promptly.
5. Prioritize Tasks Based on Risk
Not all cybersecurity tasks are equal. Some tasks are more critical than others and should be prioritized accordingly. For example, patching vulnerabilities in critical systems should take precedence over less urgent tasks. Rank tasks by risk and address the most important ones first.
6. Automate Data Entry for Efficiency
If possible, automate parts of the checklist data entry process. For example, you can link the Responsible Person field to an employee directory or use macros to generate reports automatically. This will save time and reduce the chances of errors.
7. Review and Track Progress Regularly
Hold regular meetings or reviews to discuss the progress of your cybersecurity efforts. Review the checklist with your team, identify any bottlenecks, and make adjustments as necessary. This ensures that the checklist is being used effectively.
Conclusion
A Cybersecurity Tracking Checklist in Excel is an invaluable tool for managing and tracking cybersecurity tasks. It provides a clear, organized way to monitor critical tasks, assign responsibilities, and stay on top of deadlines. By using this tool, businesses can ensure that their cybersecurity efforts are comprehensive, organized, and effective.
Whether you’re a small business owner or part of a larger organization’s IT team, a well-maintained checklist can greatly improve your cybersecurity posture. It not only simplifies the task management process but also increases accountability, enhances team collaboration, and provides real-time insights into your cybersecurity efforts.
Frequently Asked Questions (FAQ)
What is a Cybersecurity Tracking Checklist in Excel?
A Cybersecurity Tracking Checklist in Excel is a tool that helps organizations track and manage cybersecurity tasks. It enables businesses to monitor their security efforts, assign tasks, and ensure deadlines are met.
How can I customize the Cybersecurity Tracking Checklist?
The checklist can be customized by adding or removing checklist items, adjusting columns, and modifying the format in Excel to meet the specific needs of your organization.
Why should I use Excel for tracking cybersecurity tasks?
Excel is a cost-effective and flexible tool that allows easy customization, task tracking, and real-time monitoring. It also provides the ability to create visual progress indicators and task assignments with minimal effort.
How often should I update the Cybersecurity Tracking Checklist?
It is essential to update the checklist regularly to address emerging cybersecurity threats and to ensure that all tasks are aligned with current security needs.
Can I track the progress of cybersecurity tasks in real time?
Yes, the checklist includes a Progress Bar that displays the percentage of tasks completed, providing a real-time overview of your cybersecurity efforts.
Visit our YouTube channel to learn step-by-step video tutorials