In today’s digital world, businesses face increasing threats from cyberattacks, data breaches, and unauthorized access. Small organizations, as well as large enterprises, must prioritize IT security. However, managing security tasks without a structured process often leads to gaps, overlooked areas, and weak compliance.
That’s where an IT Security To-Do List Checklist in Excel becomes invaluable. This template gives you a simple, organized, and easy-to-use tool for monitoring and tracking every critical IT security activity. By using Excel, you don’t need expensive software or complex setups. You can start managing your IT security tasks immediately, whether for a small business, educational institution, or corporate IT department.
This article explores everything about the IT Security To-Do List Checklist in Excel—its features, benefits, best practices, and how it can transform your IT operations.
Click to Purchases IT Security To-Do List Checklist in Excel
What Is an IT Security To-Do List Checklist in Excel?
An IT Security To-Do List Checklist is a structured template designed in Excel that allows IT teams to plan, assign, and track security activities. The checklist acts as a central hub where you can log every task, set deadlines, assign responsibilities, and monitor progress.
Instead of relying on scattered notes, emails, or manual reminders, this checklist brings all security-related tasks into one place. With just a few clicks, IT managers can see which tasks are pending, completed, or overdue.
The best part is that this tool is built in Microsoft Excel, which means it requires no additional installation, can be easily shared, and is highly customizable for any organization.
Key Features of the IT Security To-Do List Checklist Template
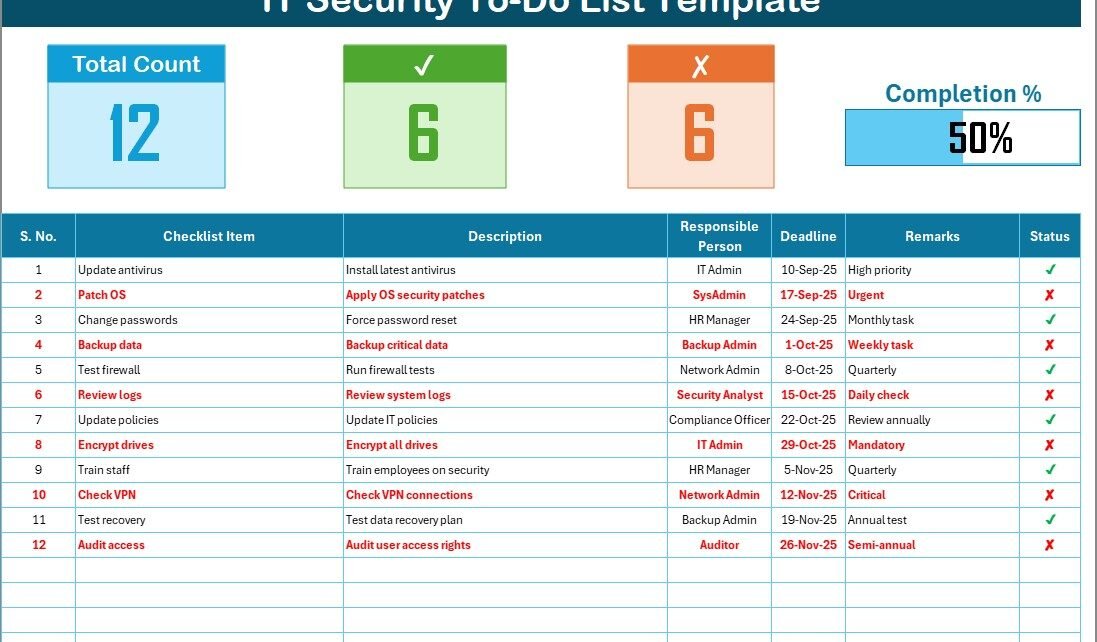
The IT Security To-Do List Checklist Template comes with two structured worksheets, each serving a specific purpose.
IT Security To-Do List Checklist Sheet Tab
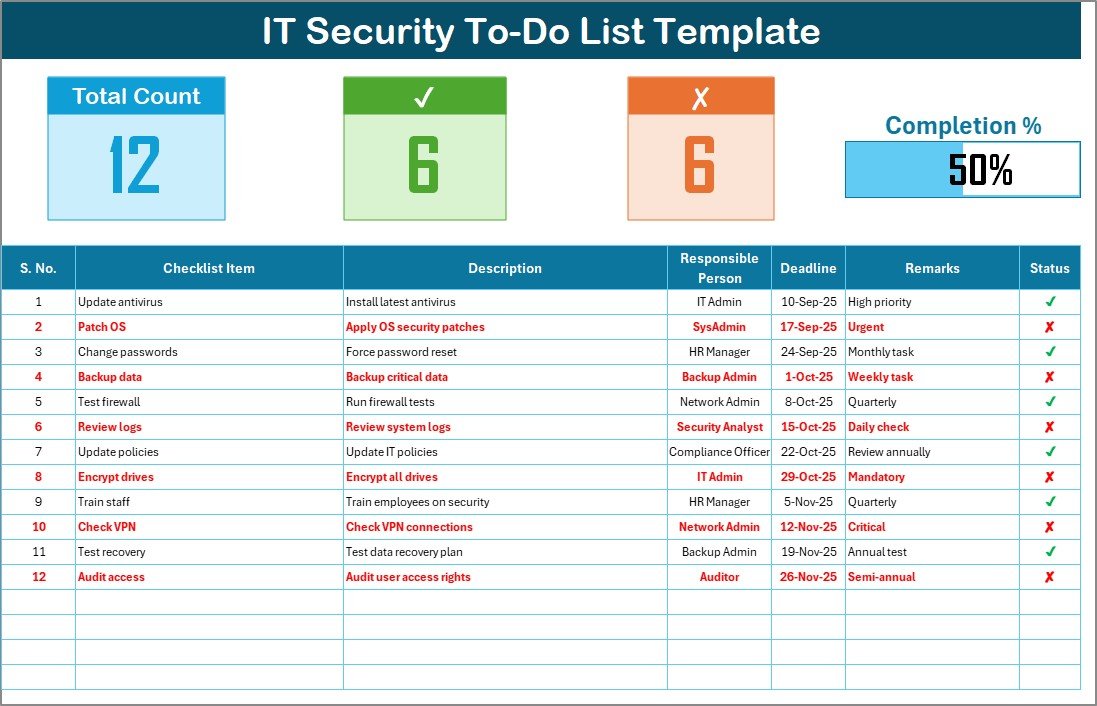
This is the main sheet tab, where all checklist details are captured.
Top Section
- Displays key summary metrics.
- Includes Total Count, Checked Count, Crossed Count, and a Progress Bar.
- The progress bar helps track how much of the checklist has been completed in percentage.
Checklist Table
This table is the core of the template. It allows you to log and track each IT security task with full details. The columns include:
- Serial No. – Unique number for each task.
- Checklist Item – Specific IT security task (e.g., “Update firewall rules”).
- Description – Brief details about the task.
- Responsible Person – Assigned team member or department.
- Deadline – Date by which the task must be completed.
- Remarks – Short notes or follow-ups.
- Status – Mark each task with ✔ for done or ✘ for pending.
List Sheet Tab
This sheet stores the unique list of responsible persons. It ensures consistency and prevents typing errors when assigning tasks in the main checklist.
By maintaining this list, drop-down selections become easier, and accountability remains clear.
Why Use an IT Security To-Do List Checklist?
Many organizations underestimate the power of a simple checklist. Yet, when it comes to IT security, even one missed step can lead to severe consequences.
Here are some key reasons to use this checklist:
-
Organization: Keeps all security tasks structured in one place.
-
Clarity: Clearly assigns tasks to team members.
-
Tracking: Tracks progress with a visual progress bar.
-
Accountability: Holds employees responsible for completing assigned tasks.
-
Compliance: Helps ensure adherence to IT security regulations and standards.
-
Efficiency: Saves time by reducing repetitive communication.
Examples of IT Security Tasks to Include in the Checklist
To maximize its value, you should populate the checklist with relevant IT security tasks. Some practical examples are:
-
Update and patch operating systems regularly.
-
Install and update antivirus software.
-
Review firewall configurations.
-
Conduct employee cybersecurity awareness training.
-
Backup critical business data.
-
Test disaster recovery plans.
-
Enforce strong password policies.
-
Monitor suspicious login attempts.
-
Remove unused user accounts.
-
Encrypt sensitive files and folders.
These tasks, once added to the checklist, help ensure no area of IT security is overlooked.
Advantages of IT Security To-Do List Checklist in Excel
Click to Purchases IT Security To-Do List Checklist in Excel
Using this checklist template brings several advantages to your organization.
✅ Simple and user-friendly – No technical expertise is required.
✅ Centralized tracking – All security activities are in one file.
✅ Visual progress monitoring – The progress bar shows completion percentage.
✅ Accountability – Assigns clear responsibility for every task.
✅ Cost-effective – Built on Excel, so no extra software costs.
✅ Customizable – Can be modified to fit industry-specific security needs.
✅ Compliance support – Helps prepare for audits and legal compliance checks.
Opportunities for Improvement in IT Security Management
While the Excel-based checklist is a great starting point, IT security management can still face challenges. Recognizing these gaps helps improve security further.
🔸 Automation – Excel is manual, but advanced tools can automate recurring tasks.
🔸 Integration – Checklist data can be linked to reporting systems or dashboards.
🔸 Scalability – As organizations grow, a database or cloud-based system may be required.
🔸 Real-time Alerts – Excel does not provide automatic alerts for overdue tasks.
🔸 Data Security – The checklist itself must be secured to prevent misuse.
By identifying these improvement areas, IT managers can gradually upgrade from Excel-based solutions to more advanced systems while still leveraging the simplicity of a checklist.
Best Practices for Using the IT Security To-Do List Checklist
To make the most out of this Excel template, organizations should follow some best practices:
🟢 Keep the checklist updated – Regularly review and update tasks.
🟢 Assign clear responsibilities – Always mention a responsible person.
🟢 Set realistic deadlines – Ensure deadlines are achievable.
🟢 Review progress weekly – Use the progress bar to track completion.
🟢 Link to security policies – Connect tasks to organizational policies.
🟢 Backup the checklist file – Ensure the Excel file is also backed up.
🟢 Train employees – Teach staff how to use the checklist correctly.
🟢 Audit periodically – Cross-check tasks with compliance requirements.
How to Implement the IT Security Checklist in Your Organization
Here’s a step-by-step guide to getting started with the checklist:
-
Download the Template – Get the ready-to-use Excel file.
-
Customize Tasks – Add tasks relevant to your business.
-
Fill the Responsible Person List – Update the List tab with team members.
-
Assign Tasks – Enter details into the checklist table.
-
Set Deadlines – Define timelines for each security task.
-
Track Progress – Use ✔ and ✘ to mark status.
-
Review Results – Check summary metrics and the progress bar.
-
Update Regularly – Keep the file updated for ongoing tasks.
Who Can Benefit from the IT Security To-Do List Checklist?
This Excel template is versatile and can help multiple roles and industries:
-
IT Managers – To track team responsibilities.
-
System Administrators – To manage updates and configurations.
-
Compliance Officers – To prepare for audits.
-
Small Business Owners – To safeguard business data.
-
Educational Institutions – To protect student and staff records.
-
Healthcare Providers – To secure patient data.
-
Corporate Teams – To ensure internal IT security practices.
Conclusion
IT security is no longer optional—it is a necessity. Data breaches, ransomware, and cyber threats continue to increase, and organizations cannot afford to leave their systems unprotected.
The IT Security To-Do List Checklist in Excel provides a simple yet powerful way to manage, track, and monitor all security activities. With structured worksheets, progress tracking, and clear accountability, this checklist ensures no task gets missed.
It is user-friendly, cost-effective, and adaptable for businesses of all sizes. By following the best practices shared in this article, you can make your IT security management stronger, more reliable, and more audit-ready.
Frequently Asked Questions (FAQs)
1. What is an IT Security To-Do List Checklist?
It is an Excel-based tool used to track and manage IT security tasks such as system updates, backups, and access controls.
2. Why should I use this checklist in Excel?
Excel is cost-effective, easy to use, and does not require advanced software. The checklist organizes all IT security tasks in one place.
3. Can I customize the checklist for my organization?
Yes. You can add or remove tasks, change deadlines, and update the responsible person list based on your organization’s needs.
4. Is this checklist suitable for small businesses?
Absolutely. Small businesses can use it to manage IT security without investing in costly tools.
5. Does the checklist replace IT security software?
No. The checklist is a management tool. It helps track activities but does not perform security functions like firewalls or antivirus programs.
6. How often should I update the checklist?
Ideally, review and update the checklist weekly to ensure no tasks are missed.
7. What happens if a task is delayed?
The remarks column can be used to record reasons for delay, and overdue tasks can be flagged for urgent attention.
8. Can I share the checklist with my team?
Yes. Since it is Excel-based, you can share the file over email, cloud storage, or collaboration tools.
9. Is the template beginner-friendly?
Yes. The template uses a simple layout and check marks for easy status updates.
10. How does this checklist support compliance?
By ensuring that critical IT security tasks are completed on time, the checklist helps organizations stay compliant with data protection laws and regulations.
Visit our YouTube channel to learn step-by-step video tutorials
Click to Purchases IT Security To-Do List Checklist in Excel
Watch the step-by-step video tutorial: