In today’s digital-first world, organizations depend heavily on IT systems to operate. However, with this reliance comes risk. Data breaches, compliance failures, and mismanaged documentation can cost businesses millions. To prevent such risks, companies must follow strict IT security documentation practices.
One of the simplest and most effective ways to organize these practices is through an IT Security Documentation Checklist in Excel. This ready-to-use tool helps businesses streamline their security processes, ensure compliance, and avoid costly mistakes.
In this detailed guide, we will explore the structure, features, benefits, best practices, and practical uses of an IT Security Documentation Checklist in Excel. We will also provide insights into how organizations can maximize its potential.
Click to Purchases IT Security Documentation Checklist in Excel
What Is an IT Security Documentation Checklist?
An IT Security Documentation Checklist is a structured list of essential security tasks, policies, and procedures that organizations need to maintain. It ensures that no critical documentation is overlooked while keeping the process simple and trackable.
Instead of relying on scattered notes or complex tools, this checklist puts everything into a single Excel file. It acts as a central hub where IT managers, administrators, and compliance teams can record, track, and update their documentation efforts.
Why Use Excel for IT Security Documentation?
Many organizations use advanced IT systems, yet when it comes to tracking compliance and documentation, Excel remains one of the most popular tools. Here’s why:
-
Ease of Use: No steep learning curve—almost everyone knows how to use Excel.
-
Flexibility: You can customize columns, formulas, and formats as per your security needs.
-
Accessibility: Excel files can be stored locally, on shared drives, or in cloud-based systems.
-
Automation: With formulas and conditional formatting, you can track progress instantly.
-
Cost-Effective: No need to purchase expensive software for basic documentation tracking.
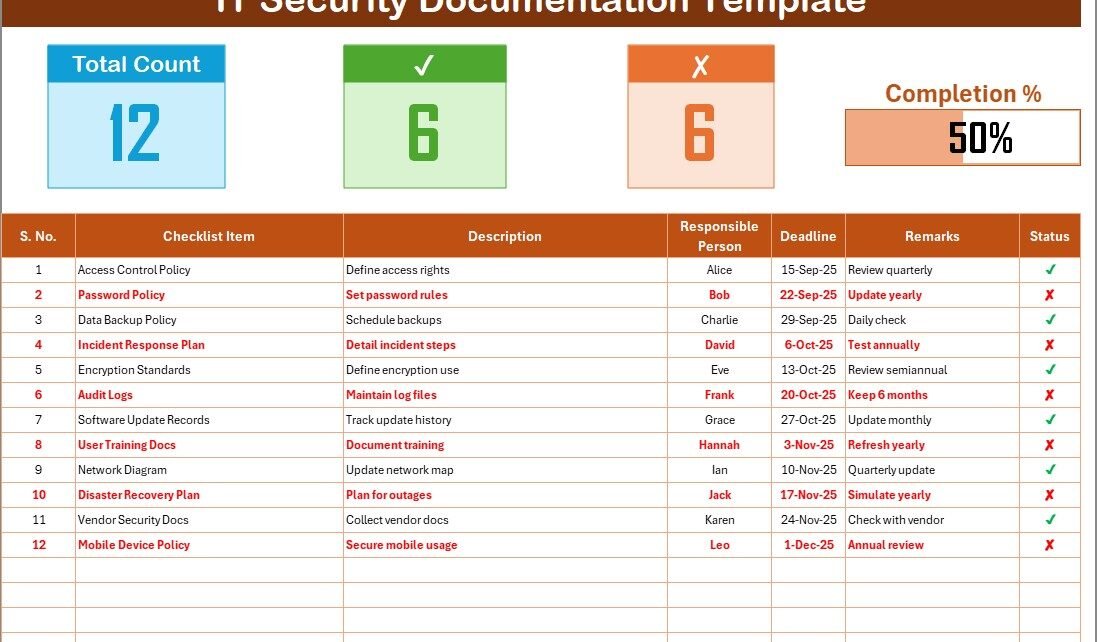
Structure of the IT Security Documentation Checklist in Excel
This template is designed to be simple, practical, and effective. It contains two main worksheets:
IT Security Documentation Checklist Sheet Tab
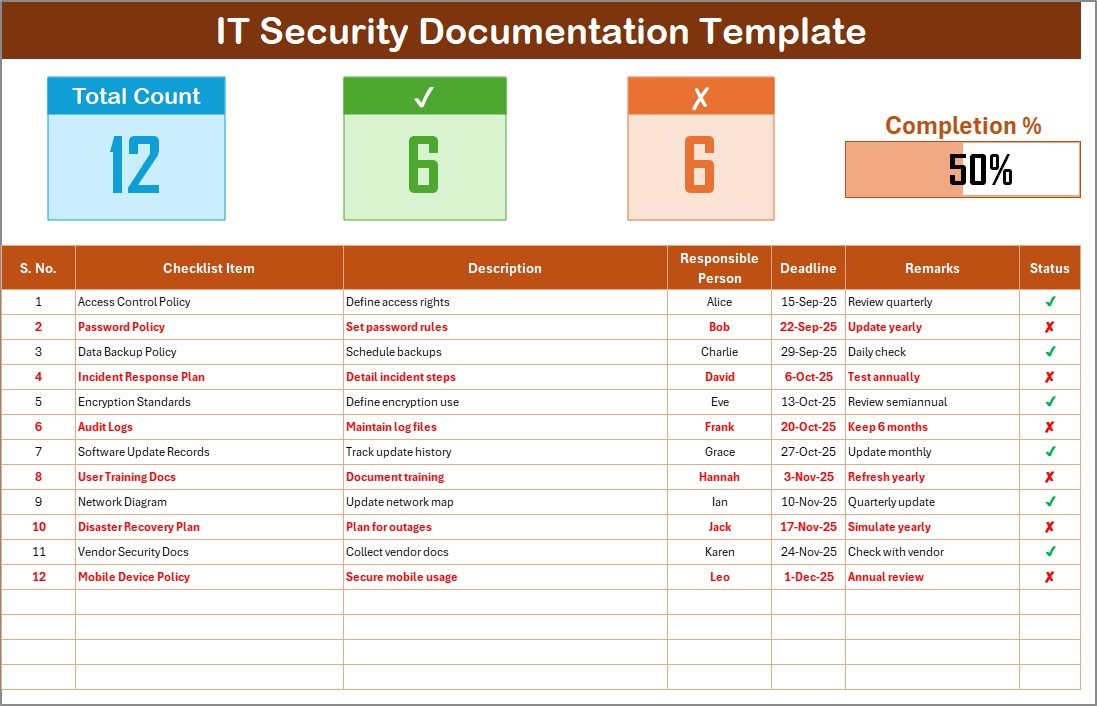
This is the main sheet where you capture all checklist details.
Top Section Features:
-
Total Count: Shows the number of items in the checklist.
-
Completed Count: Displays how many items have been marked as ✔.
-
Pending Count: Displays how many are marked as ✘.
-
Progress Bar: A visual tracker that shows the percentage of completion.
Checklist Table Columns:
-
Serial No. – Unique identifier for each item.
-
Checklist Item – The task or documentation requirement.
-
Description – Short explanation of the task.
-
Responsible Person – Who is accountable for completing it.
-
Deadline – The due date for completion.
-
Remarks – Notes, clarifications, or special instructions.
-
Status – Marked as ✔ for completed or ✘ for pending.
List Sheet Tab
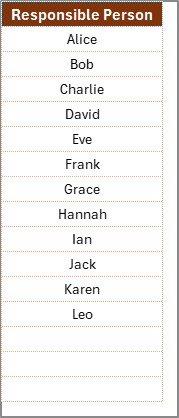
This sheet captures the unique list of responsible persons. It supports dropdown menus in the main checklist, making the process cleaner and reducing manual errors.
Advantages of IT Security Documentation Checklist
Implementing this checklist provides multiple benefits for businesses:
✅ Ensures Compliance: Keeps security processes aligned with industry standards like ISO, GDPR, or HIPAA.
✅ Reduces Risk: Prevents missed documentation that could lead to vulnerabilities.
✅ Boosts Accountability: Assigns clear responsibilities to individuals.
✅ Improves Efficiency: Saves time by centralizing all security tasks in one file.
✅ Tracks Progress: Visual indicators help managers see what’s pending and what’s complete.
✅ Cost-Effective Solution: Eliminates the need for costly compliance management software.
Click to Purchases IT Security Documentation Checklist in Excel
Key Use Cases of the Checklist
Organizations across industries can benefit from this Excel tool. Some practical use cases include:
-
Data Security Compliance: Ensuring that policies are updated and audits are completed.
-
Disaster Recovery Planning: Tracking backup schedules and documentation of recovery protocols.
-
Access Control Management: Monitoring employee access rights and approvals.
-
Incident Response Readiness: Ensuring all reporting forms and workflows are documented.
-
IT Policy Management: Keeping IT policies updated and version-controlled.
How to Use the IT Security Documentation Checklist
Using this template is simple. Here’s a step-by-step process:
-
Open the Excel File: Start with the prebuilt template.
-
Enter Checklist Items: Fill in the security tasks you want to track.
-
Assign Responsibilities: Use the dropdown to assign tasks to team members.
-
Set Deadlines: Add due dates for each item.
-
Update Status: Mark ✔ for completed or ✘ for pending.
-
Review Progress: Check the progress bar for overall completion.
-
Conduct Regular Reviews: Update the file after every audit or compliance review.
Opportunities for Improvement
While the template is powerful, organizations can enhance it further by:
🔹 Integrating with SharePoint or Google Drive for real-time collaboration.
🔹 Adding conditional alerts when deadlines are near.
🔹 Using pivot tables and charts for visual reports.
🔹 Linking with incident trackers for a full IT security ecosystem.
🔹 Setting version history for audit tracking.
Best Practices for the IT Security Documentation Checklist
To maximize the effectiveness of this tool, follow these best practices:
-
Keep It Updated: Review and update the checklist regularly.
-
Assign Accountability Clearly: Ensure every task has a responsible person.
-
Use Short Descriptions: Keep descriptions under 70 characters for clarity.
-
Review Deadlines Often: Adjust due dates as project scopes evolve.
-
Leverage Automation: Use Excel formulas for faster calculations and tracking.
-
Conduct Periodic Audits: Compare the checklist against compliance requirements.
Conclusion
The IT Security Documentation Checklist in Excel is a practical, cost-effective, and easy-to-use solution for businesses of all sizes. By centralizing IT security documentation into one structured file, organizations can ensure compliance, reduce risks, and improve efficiency.
This tool not only makes tracking simple but also builds accountability within the team. Whether you are a small business, an IT department, or a compliance officer, this checklist can significantly improve the way you manage IT security documentation.
Frequently Asked Questions (FAQs)
1. What is the purpose of an IT Security Documentation Checklist?
It helps organizations track, manage, and ensure all IT security documents are complete and compliant with regulations.
2. Who should use this checklist?
IT managers, compliance officers, system administrators, and auditors can all use this checklist.
3. Can I customize the checklist?
Yes, the Excel format is flexible—you can add, remove, or modify columns and tasks.
4. How does the progress bar work?
The progress bar updates automatically based on the number of completed tasks marked with ✔.
5. Is this checklist suitable for small businesses?
Absolutely. Small businesses can use it to avoid missing important documentation and stay compliant.
6. Can this checklist replace compliance management software?
For basic documentation tracking, yes. However, large enterprises may still need advanced tools for automation and integration.
7. How often should I update the checklist?
Ideally, after every audit cycle or whenever a major IT change takes place.
8. Can I use this checklist for ISO or GDPR compliance?
Yes. By customizing the checklist items, you can align it with ISO 27001, GDPR, HIPAA, or other security frameworks.
Visit our YouTube channel to learn step-by-step video tutorials