In today’s digital landscape, safeguarding sensitive information and ensuring the security of systems is paramount. One of the most effective ways to ensure your organization’s cybersecurity measures are up to standard is through detailed documentation. A well-organized Cybersecurity Documentation Checklist in Excel can be a game-changer, helping businesses manage and monitor their security practices effectively. This guide will walk you through everything you need to know about using this checklist template to boost your cybersecurity efforts.
Click to Purchases Cybersecurity Documentation Checklist in Excel
What is a Cybersecurity Documentation Checklist?
A Cybersecurity Documentation Checklist is a structured tool used to ensure all necessary steps and protocols are in place to protect digital assets from cyber threats. It acts as a reference point to ensure all cybersecurity measures are followed, tracked, and regularly updated.
The Cybersecurity Documentation Checklist in Excel template helps organizations document their cybersecurity actions, track their progress, and maintain a clear record of tasks and responsibilities. It’s an essential tool for maintaining compliance with various cybersecurity standards and regulations.
Key Features of the Cybersecurity Documentation Checklist Template
This ready-to-use Cybersecurity Documentation Checklist template in Excel comes with a comprehensive structure to streamline your cybersecurity efforts. It features two essential worksheets:
Cybersecurity Documentation Checklist Sheet Tab
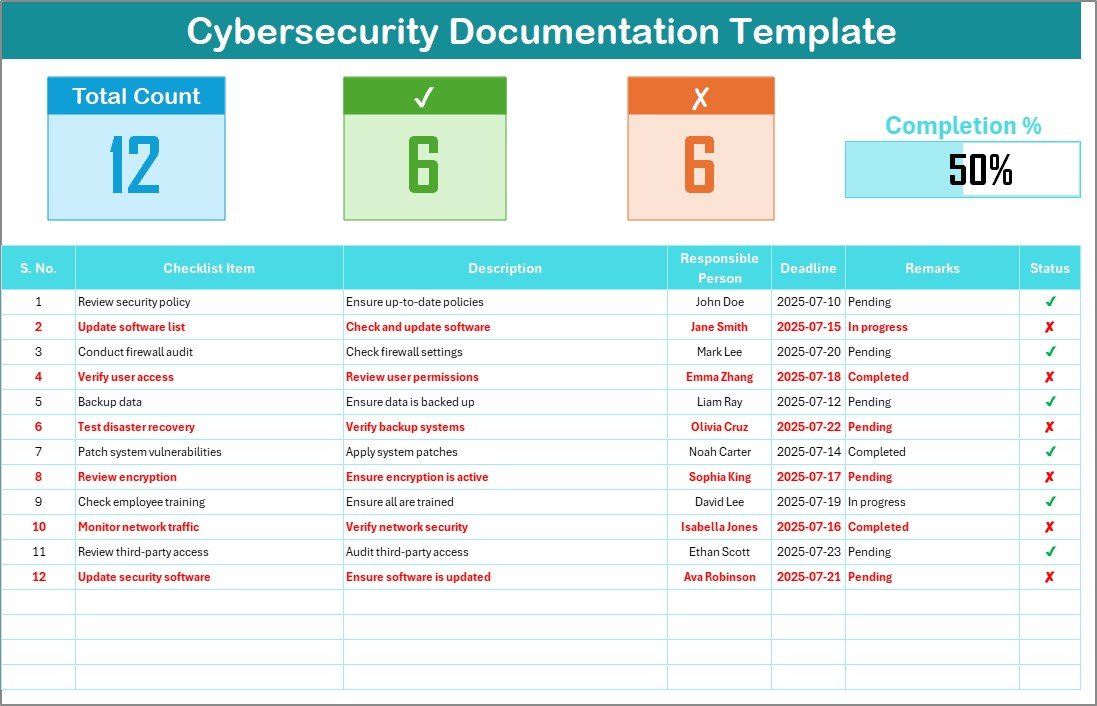
This is the main sheet where you will capture all the necessary checklist items related to cybersecurity. The layout of this sheet is designed to help you track and manage tasks efficiently.
Top Section Overview:
At the top of the sheet, you’ll find essential data points that provide an at-a-glance overview of the checklist’s progress. This includes:
-
Total Count: This represents the total number of items in the checklist.
-
Checked Count: The number of tasks that have been completed successfully.
-
Crossed Count: The tasks that were marked as not applicable or irrelevant.
-
Progress Bar for Checked %: A visual representation of how much of the checklist has been completed, making it easy to see your progress at a glance.
Checklist Table:
The core of the checklist is the table, where each task and its status are documented. The table includes the following columns:
-
Serial No.: A unique identifier for each checklist item.
-
Checklist Item: A brief description of the task or requirement.
-
Description: A detailed explanation of the task, including necessary steps to complete it.
-
Responsible Person: The individual assigned to complete the task.
-
Deadline: The due date for completing the task.
-
Remarks: Additional notes or comments related to the task.
-
Status: The status of the task, marked as either ✔ (completed) or ✘ (not completed or not applicable).
This sheet ensures that all necessary cybersecurity tasks are documented and tracked, providing transparency and accountability within the organization.
List Sheet Tab
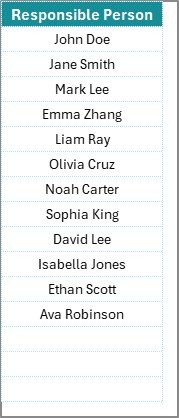
This sheet is dedicated to managing the list of responsible persons. It helps create a drop-down list in the main checklist sheet, ensuring consistency and reducing manual data entry errors.
By having a dedicated list of responsible persons, the template allows for quick assignment of tasks and easy tracking of who is responsible for each cybersecurity measure.
Advantages of Using a Cybersecurity Documentation Checklist in Excel
Using a Cybersecurity Documentation Checklist in Excel provides numerous benefits to your organization, ensuring that your cybersecurity measures are comprehensive, up-to-date, and well-documented. Let’s explore the advantages:
1. Streamlined Task Management
The checklist format helps break down complex cybersecurity tasks into manageable steps, making it easier for teams to focus on individual tasks. It provides clear deadlines, responsibilities, and status tracking, promoting efficiency.
2. Improved Accountability
With a dedicated “Responsible Person” column and clear deadlines, the checklist fosters accountability. Each task is assigned to a specific person, ensuring no task is overlooked.
3. Easy Tracking and Monitoring
The progress bar and check/cross count provide a clear visual representation of how much has been completed and what’s left to do. It enables managers to monitor progress in real time, making it easier to address any issues promptly.
4. Better Compliance
Maintaining a cybersecurity checklist helps organizations stay compliant with various industry standards and regulations (such as GDPR, HIPAA, and NIST). A well-documented checklist ensures that all required security measures are in place and can be easily reviewed during audits.
5. Flexibility and Customization
Excel’s flexibility allows users to tailor the checklist according to their specific needs. You can add or remove tasks, adjust deadlines, and modify the structure of the template as necessary. This makes the template adaptable to any organization’s cybersecurity requirements.
Best Practices for Maintaining a Cybersecurity Documentation Checklist
To get the most out of your Cybersecurity Documentation Checklist in Excel, it’s important to follow best practices that ensure the tool remains effective and up to date. Here are some tips for managing your checklist efficiently:
1. Regularly Update the Checklist
Cybersecurity threats evolve, and so should your documentation. Regularly update your checklist to reflect new cybersecurity measures, tasks, or compliance requirements. This ensures your checklist is always relevant and actionable.
2. Ensure Clear Task Descriptions
For each item in the checklist, provide clear and concise descriptions of the task. The easier it is for the responsible person to understand the task, the more likely it is that the task will be completed on time and accurately.
3. Assign Tasks Based on Expertise
Assign cybersecurity tasks to individuals who have the relevant skills and expertise. For example, tasks related to network security should be handled by someone with networking experience. Proper task allocation ensures efficiency and effective completion of tasks.
4. Use Conditional Formatting for Status
In Excel, you can use conditional formatting to change the color of cells based on the task’s status (e.g., green for ✔, red for ✘). This makes it easier to visually track which tasks are completed and which are still pending.
5. Backup Your Document Regularly
Excel files are susceptible to data loss due to system failures. Ensure that you regularly back up your cybersecurity checklist to avoid losing valuable data. You can also consider storing it on a cloud platform to make it accessible and secure.
6. Review and Audit the Checklist Periodically
To ensure the checklist remains accurate and up-to-date, schedule regular reviews and audits. This allows you to spot any outdated tasks, incomplete items, or missed actions that could compromise your organization’s cybersecurity posture.
Conclusion
The Cybersecurity Documentation Checklist in Excel is an indispensable tool for any organization serious about protecting its digital assets. With its structured format, ease of use, and ability to track progress and accountability, it helps streamline cybersecurity efforts and ensures compliance with industry standards. By incorporating the best practices outlined above, you can maximize the effectiveness of your cybersecurity documentation, ensuring your organization stays protected in an ever-evolving cyber landscape.
Click to Purchases Cybersecurity Documentation Checklist in Excel
Frequently Asked Questions (FAQs)
1. What is the purpose of a Cybersecurity Documentation Checklist?
A Cybersecurity Documentation Checklist helps organizations ensure all necessary security measures are in place, tracked, and documented. It promotes accountability and compliance while streamlining task management.
2. How does the Excel template improve task management?
The Excel template organizes tasks, assigns responsibilities, and tracks deadlines, making it easier to manage and monitor cybersecurity measures. The progress bar and status indicators offer a visual way to track completion.
3. Can I customize the checklist for my organization’s needs?
Yes, the template is highly customizable. You can add or remove tasks, adjust deadlines, and modify the structure to suit your specific cybersecurity needs.
4. How often should I update the Cybersecurity Documentation Checklist?
It’s important to update the checklist regularly to keep up with new cybersecurity threats, technologies, and compliance regulations. Frequent updates ensure the checklist remains relevant and effective.
5. Is the checklist useful for maintaining compliance with cybersecurity standards?
Yes, the checklist helps organizations stay compliant with various cybersecurity standards and regulations by ensuring all required security measures are documented and implemented.
Visit our YouTube channel to learn step-by-step video tutorials