In today’s digital world, cybersecurity is not an option—it is a necessity. Organizations of all sizes face continuous threats from phishing, ransomware, unauthorized access, and data breaches. If not managed properly, these risks can lead to financial loss, reputational damage, and even legal consequences.
One effective way to strengthen defenses is to use an IT Security Monitoring Checklist in Excel. This structured tool ensures that every task, responsibility, and security measure gets tracked and completed on time. With Excel’s flexibility, businesses can build an actionable checklist that keeps IT operations transparent, accountable, and efficient.
Click to Purchases IT Security Monitoring Checklist in Excel
In this article, we will explore:
-
What an IT Security Monitoring Checklist is.
-
How this Excel template works.
-
Advantages of using it.
-
Best practices to follow.
-
Practical use cases for different industries.
-
FAQs to clarify common doubts.
By the end, you will know exactly how to use this checklist to keep your systems secure and compliant.
What Is an IT Security Monitoring Checklist in Excel?
An IT Security Monitoring Checklist in Excel is a ready-to-use template designed to help IT teams, compliance officers, and managers track security-related activities. Instead of relying on manual notes or expensive software, this Excel-based tool centralizes all tasks in one file.
It records essential details like:
-
Checklist items (security actions to perform).
-
Short descriptions of the tasks.
-
Responsible persons for accountability.
-
Deadlines to ensure timely action.
-
Status indicators (✔ or ✘).
-
A progress bar to visualize completion rate.
This makes it easy to monitor IT processes such as patch updates, access reviews, backups, vulnerability scans, and more.
Structure of the Template
The template includes two main worksheets:
IT Security Monitoring Checklist Sheet
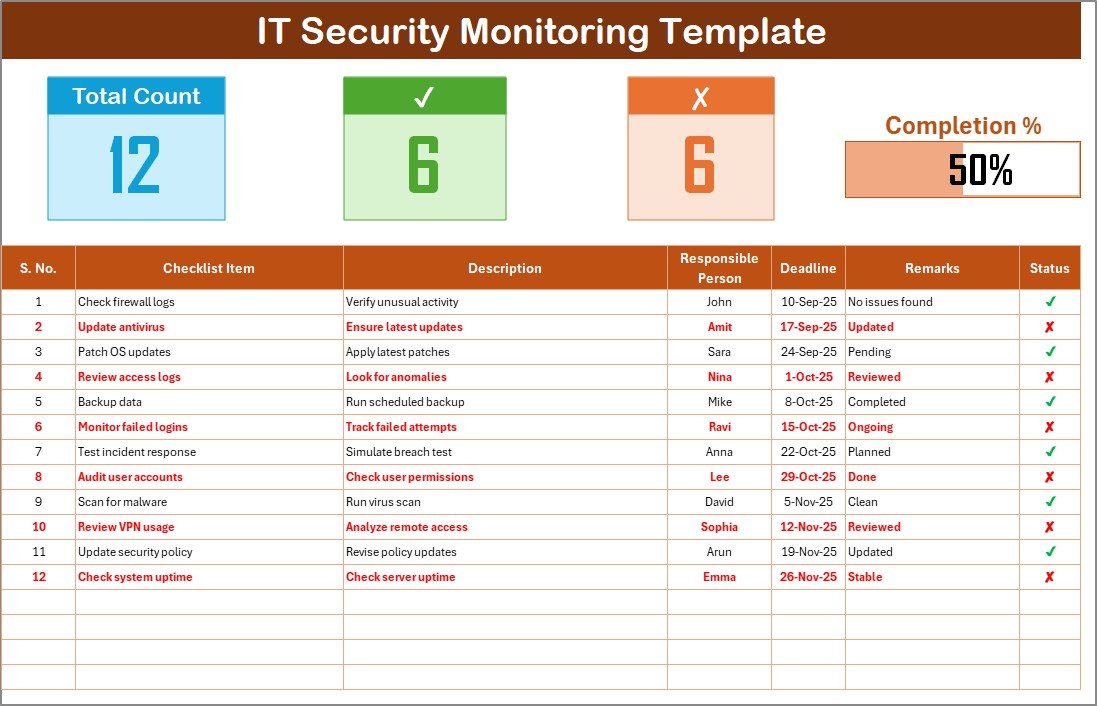
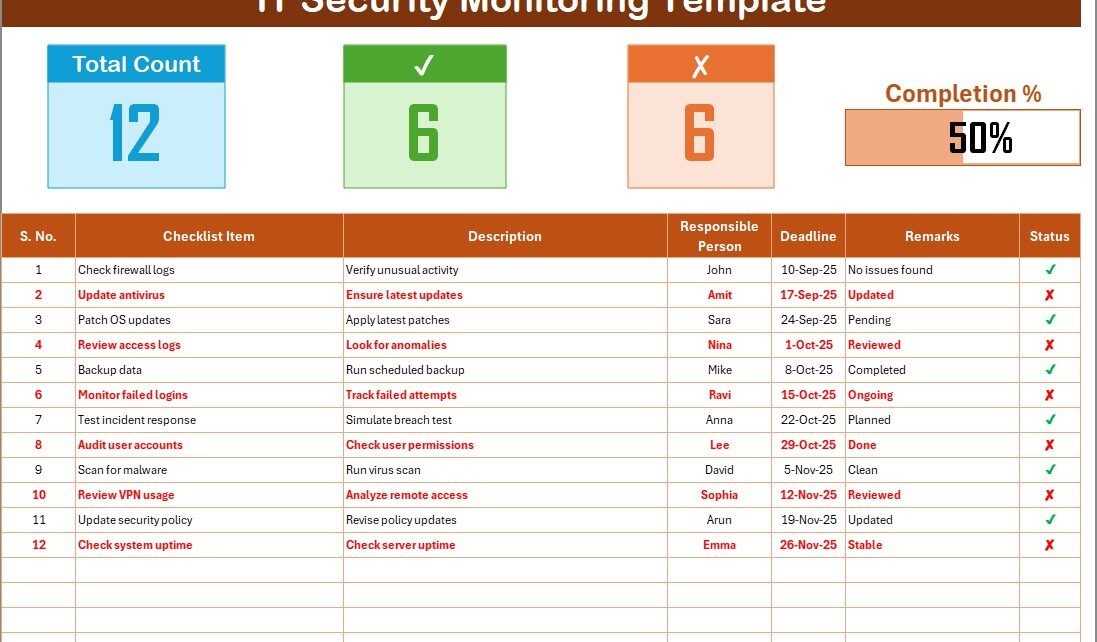
This is the core of the template where all tasks are captured.
Top Section Features:
-
Total Count – Total number of tasks.
-
Checked Count – Completed items.
-
Crossed Count – Incomplete items.
-
Progress Bar – Visual representation of completion percentage.
Checklist Table Columns:
-
Serial No. – Unique identifier for each task.
-
Checklist Item – The activity to monitor (e.g., password policy review).
-
Description – Short details of the task.
-
Responsible Person – Assigned staff member.
-
Deadline – Due date for the task.
-
Remarks – Notes or updates.
-
Status – Marked as ✔ (done) or ✘ (not done).
This structured layout ensures nothing gets missed and every action is clearly documented.
List Sheet
This secondary sheet captures the unique list of responsible persons. It is linked to the main checklist table through drop-down menus, making task assignment quick and error-free.
By separating names in a list, organizations can maintain clean data entry and avoid duplication.
Why Do You Need an IT Security Monitoring Checklist?
Many businesses believe that investing in firewalls or antivirus software is enough. However, without regular monitoring, even the best tools fail. That is where this checklist becomes valuable.
Here are the main reasons you need it:
-
Consistency – Security activities become routine instead of random.
-
Accountability – Clear responsibility ensures no task is overlooked.
-
Compliance – Helps meet regulatory requirements like ISO, GDPR, HIPAA, or PCI DSS.
-
Efficiency – Saves time by providing a single dashboard for monitoring.
-
Visibility – Managers get a complete picture of progress at a glance.
Key Features of the IT Security Monitoring Checklist in Excel
When you use this template, you benefit from several practical features:
-
Interactive progress tracking with real-time status updates.
-
Drop-down assignment of responsible persons for accuracy.
-
Customizable checklist items to fit your business needs.
-
Clear deadlines for prioritization.
-
Visual progress bar to encourage timely completion.
-
User-friendly Excel layout that requires no coding or technical setup.
Advantages of IT Security Monitoring Checklist in Excel
Click to Purchases IT Security Monitoring Checklist in Excel
Using this checklist brings both technical and organizational benefits.
📌 Advantages:
-
Ensures all security tasks are completed on time.
-
Improves collaboration between IT, compliance, and management teams.
-
Reduces the chance of security incidents due to missed steps.
-
Provides audit-ready documentation for regulators.
-
Saves money compared to expensive monitoring software.
-
Increases employee accountability with assigned responsibilities.
-
Offers flexibility to adapt to different IT environments.
Best Practices for Using the Checklist
To maximize effectiveness, follow these proven best practices:
-
Keep the checklist updated – Add new tasks as threats evolve.
-
Assign tasks wisely – Ensure responsible persons have the right expertise.
-
Review deadlines regularly – Adjust based on business needs.
-
Use conditional formatting – Highlight overdue tasks in red for visibility.
-
Integrate with team meetings – Discuss progress during weekly reviews.
-
Back up the file – Store copies securely to avoid loss.
-
Link to compliance goals – Align checklist items with regulatory frameworks.
How Different Industries Can Use It
1. Small Businesses
Helps track basic security tasks like system updates, backup checks, and password policy reviews without needing costly software.
2. Healthcare
Keeps compliance with HIPAA by tracking patient data protection activities and system audits.
3. Finance & Banking
Ensures strict monitoring of customer data, fraud detection, and regulatory reporting.
4. Education
Supports schools and universities in monitoring IT labs, student data, and staff access controls.
5. Corporate Enterprises
Provides a scalable way to manage large IT security teams, policies, and global compliance requirements.
How to Customize the Checklist
One of the biggest advantages of Excel is customization. You can:
-
Add more columns such as Priority, Risk Level, or Verification Steps.
-
Create pivot tables to analyze performance by department or person.
-
Apply filters for quick searching (e.g., show only overdue tasks).
-
Insert charts for a visual summary of security health.
-
Use formulas to calculate completion percentage automatically.
Step-by-Step: How to Use the Template
-
Open the template and review the default checklist.
-
Enter checklist items such as “Firewall Configuration Audit.”
-
Assign responsible persons using the drop-down list.
-
Set deadlines to ensure timely completion.
-
Update status with ✔ when done or ✘ if pending.
-
Track progress using the automatic bar at the top.
-
Review weekly to identify overdue tasks and risks.
Opportunities for Improvement
Although the checklist is powerful, there is always room to improve:
-
Automate alerts by linking Excel with Outlook reminders.
-
Use cloud platforms like OneDrive or Google Drive for real-time collaboration.
-
Combine with Power BI dashboards for advanced visualization.
-
Expand into a larger IT Governance Framework by connecting with other trackers.
Conclusion
The IT Security Monitoring Checklist in Excel is more than just a spreadsheet—it is a practical security management system. It helps organizations monitor, document, and complete critical IT security tasks with clarity and accountability.
Instead of relying on memory or scattered notes, this tool provides a structured, easy-to-use format. It strengthens compliance, reduces risks, and ensures teams stay on track.
If you want to enhance your IT security posture without investing in expensive systems, start with this Excel-based checklist. It’s simple, affordable, and highly effective.
Frequently Asked Questions (FAQs)
1. What is the purpose of an IT Security Monitoring Checklist?
It ensures all IT security tasks are tracked, assigned, and completed on time, reducing risks and improving compliance.
2. Can small businesses use this checklist?
Yes, it is ideal for small businesses because it is affordable, easy to use, and customizable.
3. Is this Excel checklist compliant with regulations?
The template itself is not a compliance certificate, but you can align tasks with standards like ISO, GDPR, HIPAA, or PCI DSS.
4. How often should the checklist be updated?
Update it monthly or whenever new threats, policies, or technologies are introduced.
5. Can the checklist be shared with multiple team members?
Yes, by saving it on cloud platforms (e.g., OneDrive, Google Drive, SharePoint), multiple users can update it in real-time.
6. Can I add more fields to the checklist?
Absolutely. You can add fields such as Risk Level, Priority, or Verification Notes to suit your organization’s needs.
7. Does this replace advanced security software?
No, it complements existing tools by ensuring tasks are monitored and responsibilities are clear.
8. How does the progress bar work?
The bar updates automatically based on the number of ✔ (completed) tasks compared to the total tasks.
Visit our YouTube channel to learn step-by-step video tutorials