In today’s digital world, businesses deal with endless cyber threats. From phishing attempts to ransomware attacks, every organization faces risks that can disrupt operations and compromise sensitive information. One effective way to manage these risks is by creating a structured IT Security Tracking Checklist in Excel.
This article explains how you can use an Excel-based checklist to strengthen your IT security posture. We will explore its structure, features, advantages, best practices, and real-world applications. By the end, you will understand why this tool is a must-have for IT administrators, compliance managers, and business leaders.
Click to Purchases IT Security Tracking Checklist in Excel
What Is an IT Security Tracking Checklist in Excel?
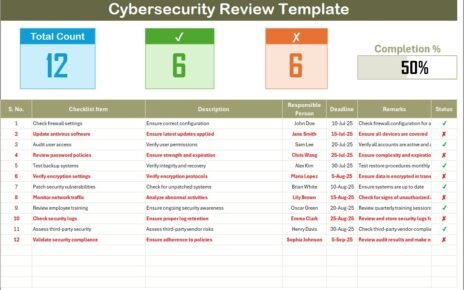
An IT Security Tracking Checklist in Excel is a prebuilt template designed to track, monitor, and update critical security tasks. Instead of relying on manual notes or complex systems, this Excel file provides a central place to record all IT security activities.
The template is user-friendly, customizable, and ready to use. It ensures accountability by assigning responsibilities and deadlines, while also making it easy to track progress with visual indicators.
Key Features of the IT Security Tracking Checklist
The template comes with two worksheets that cover everything you need:
IT Security Tracking Checklist Sheet

This is the main sheet tab where all the checklist details are managed.
Top Section Overview
- Total Count of tasks
- Checked Count (✔)
- Crossed Count (✘)
- A dynamic progress bar that visually represents task completion percentage
Checklist Table
The heart of the sheet where security items are listed with the following columns:
- Serial No.
- Checklist Item
- Description
- Responsible Person
- Deadline
- Remarks
- Status (✔ or ✘)
List Sheet Tab

This sheet stores a unique list of Responsible Persons. It powers the drop-down menus in the main checklist, making it easier to assign tasks without typing errors.
Why Do Businesses Need an IT Security Tracking Checklist?
Click to Purchases IT Security Tracking Checklist in Excel
Modern organizations rely heavily on IT infrastructure. However, without a system to track security measures, critical gaps may remain unnoticed. An IT Security Tracking Checklist helps in the following ways:
-
Ensures consistent monitoring of IT systems
-
Assigns clear responsibility for each task
-
Tracks deadlines to avoid delays
-
Provides a visual progress indicator for managers
-
Simplifies compliance audits and reporting
Advantages of Using an IT Security Tracking Checklist in Excel
✔ Centralized Tracking – All security-related tasks are documented in one place.
✔ Simple to Use – Excel is widely known, so no extra training is required.
✔ Accountability – Each task has a responsible person assigned.
✔ Deadline Management – Timelines ensure tasks are completed on schedule.
✔ Customization – The checklist can be tailored to match company-specific policies.
✔ Visual Monitoring – Progress bar and counts provide instant insights.
✔ Audit Ready – Makes compliance reporting smooth and quick.
How to Create and Use the Checklist Effectively
Step 1 – Define Security Categories
Break down IT security into categories like:
-
Network Security
-
Data Protection
-
Access Control
-
Incident Response
-
Compliance
Step 2 – Add Checklist Items
Fill each category with specific tasks. For example:
-
Ensure firewall rules are updated
-
Test backup restoration
-
Review user access rights
-
Apply system patches
Step 3 – Assign Responsibility
Use the drop-down list to assign each task to a responsible person.
Step 4 – Track Deadlines
Set realistic deadlines for each activity to ensure timely completion.
Step 5 – Update Status
Mark ✔ when complete, or ✘ if pending/failed. The progress bar updates automatically.
Best Practices for IT Security Tracking Checklist in Excel
-
Keep It Updated – Review and update the checklist weekly or monthly.
-
Use Color Coding – Highlight overdue tasks in red, upcoming deadlines in yellow.
-
Integrate with Policies – Align tasks with internal IT security policies.
-
Involve Stakeholders – Ensure IT admins, compliance officers, and managers all use the same file.
-
Automate Where Possible – Use Excel formulas or conditional formatting for alerts.
-
Back Up the File – Keep a secure copy to prevent accidental loss.
Opportunities for Improvement
While Excel is powerful, some areas can be enhanced:
-
Add macro automation for reminders.
-
Integrate with Outlook or Teams for notifications.
-
Link with a risk assessment sheet to prioritize tasks.
-
Use pivot charts for advanced visualization.
-
Connect with a SharePoint or cloud system for multi-user access.
Real-World Use Cases
-
Small Businesses – Track antivirus updates, backup schedules, and patch management.
-
Corporate IT Teams – Manage large-scale compliance activities.
-
Healthcare – Ensure HIPAA-related IT tasks are covered.
-
Financial Services – Monitor security controls for regulatory compliance.
-
Educational Institutions – Secure student and faculty data.
Conclusion
The IT Security Tracking Checklist in Excel is a simple yet powerful tool. It ensures tasks are completed on time, responsibilities are clear, and audits are stress-free. With its customizable design and progress tracking features, this template can fit any organization, whether small or large.
Adopting this system means fewer overlooked risks, better accountability, and stronger overall IT security.
Frequently Asked Questions (FAQs)
1. What is an IT Security Tracking Checklist?
It is an Excel-based template that helps track IT security tasks, responsibilities, and deadlines.
2. Who should use this checklist?
IT administrators, compliance managers, small businesses, and enterprises can all benefit from it.
3. Can I customize the checklist?
Yes, you can easily add, edit, or remove tasks to suit your organization’s needs.
4. How does the progress bar work?
It updates automatically based on the number of ✔ vs ✘ in the status column.
5. Is Excel enough for IT security management?
For small and medium businesses, Excel works well. Large enterprises may integrate it with advanced tools for better automation.
6. How often should I update the checklist?
Ideally, review it weekly or after every major IT change.
7. Can this help with audits?
Yes, it provides documented evidence of security tasks, making audits easier.
Visit our YouTube channel to learn step-by-step video tutorials