In today’s digital landscape, cybersecurity is more critical than ever. As businesses face growing threats from cyberattacks, it’s essential to implement effective security measures. One of the best ways to ensure that your cybersecurity protocols are robust and up to date is by using a Cybersecurity Planner Checklist. This article will explore the importance of having a checklist, its advantages, best practices, and how to use a Cybersecurity Planner Template in Excel to stay ahead of potential threats.
Click to Purchases Cybersecurity Planner Checklist in Excel
What is a Cybersecurity Planner Checklist?
A Cybersecurity Planner Checklist is a structured tool designed to help organizations and individuals track and manage cybersecurity measures and tasks. The checklist typically includes a series of actions, responsibilities, deadlines, and other key details that ensure no aspect of cybersecurity is overlooked.
The checklist ensures a systematic approach to securing networks, systems, and data, helping teams stay on top of tasks and responsibilities. By integrating this checklist into an Excel template, businesses can make the process even more efficient and user-friendly.
Key Features of the Cybersecurity Planner Template
The Cybersecurity Planner Template in Excel comes with several features that make tracking cybersecurity tasks straightforward. Here are the main features of this template:
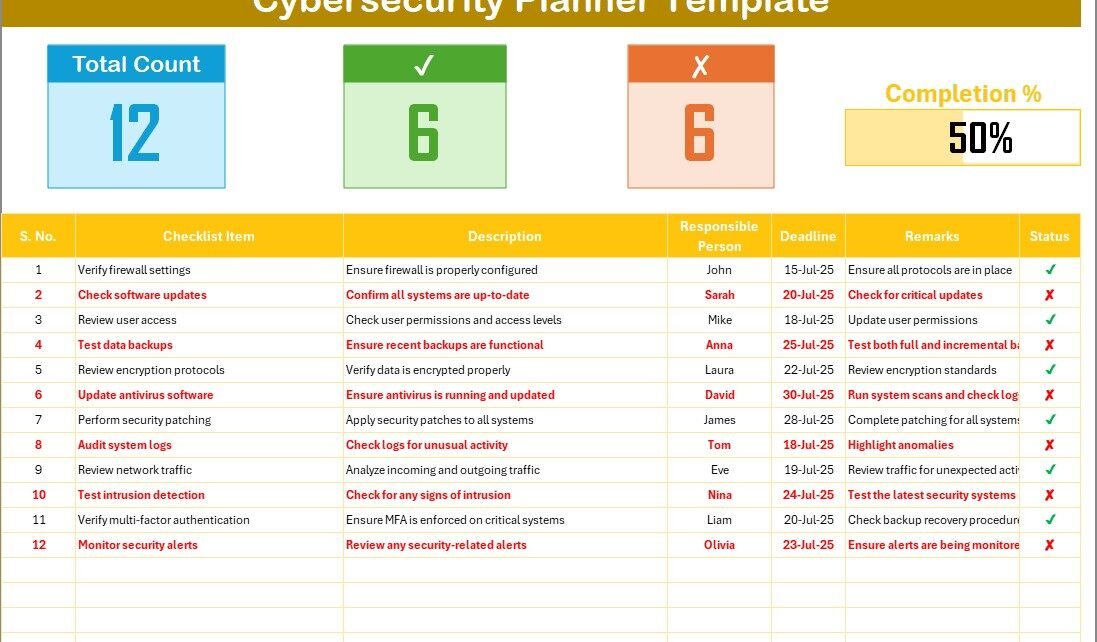
Cybersecurity Planner Checklist Sheet Tab:
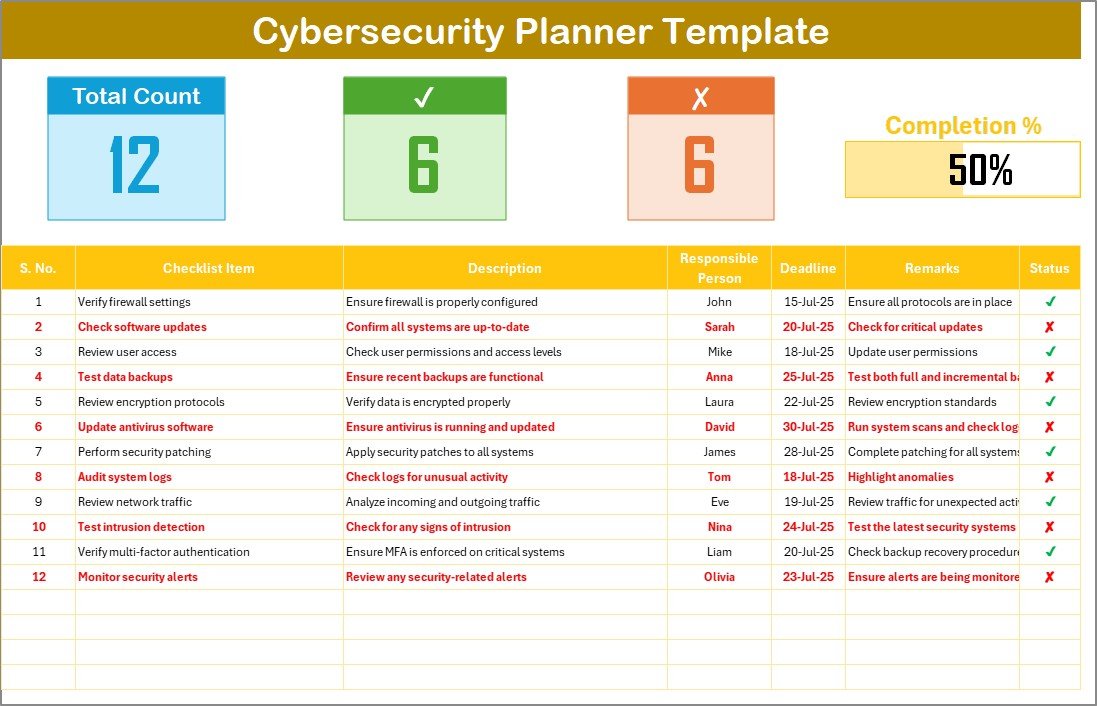
This is the primary sheet where you capture all your checklist information.
Top Section:
-
-
-
Total Count: Displays the total number of tasks in the checklist.
-
Checked Count: Shows the number of completed tasks.
-
Crossed Count: Represents the tasks that have been marked as irrelevant or not applicable.
-
Progress Bar: A visual indicator of your progress as tasks are checked off.
-
-
Checklist Table:
The checklist includes columns for:
-
-
-
Serial No.: A unique identifier for each task.
-
Checklist Item: The task or action to be performed.
-
Description: A brief explanation of the task.
-
Responsible Person: The individual or team responsible for the task.
-
Deadline: The due date for the task completion.
-
Remarks: Additional notes or clarifications related to the task.
-
Status: Indicates whether the task is completed (✔) or not (✘).
-
-
List Sheet Tab:
- This tab captures the unique list of responsible persons. This information is used to create a dropdown list in the main table, ensuring consistency and reducing the risk of errors.
Click to Purchases Cybersecurity Planner Checklist in Excel
Advantages of Using a Cybersecurity Planner Checklist
Using a Cybersecurity Planner Checklist provides several key benefits to organizations of all sizes. Here are the main advantages:
-
Improved Task Management: With a checklist, you can ensure that all cybersecurity tasks are accounted for and tracked. The ability to assign responsibilities and set deadlines makes managing these tasks easier.
-
Enhanced Security Posture: By following a structured approach, businesses can minimize the risk of overlooking critical security measures. This can help identify potential vulnerabilities before they are exploited.
-
Clear Accountability: The checklist clearly identifies who is responsible for each task, reducing confusion and ensuring that individuals are held accountable for completing their tasks on time.
-
Progress Tracking: The built-in progress bar and counters (Total Count, Checked Count, etc.) help monitor the overall progress of your cybersecurity initiatives, making it easier to identify bottlenecks and areas that need attention.
-
Customizable: The Excel template is fully customizable, allowing you to adjust the checklist according to the specific needs of your business or organization.
-
Ease of Use: Excel is a widely-used tool, and its features, such as drop-down lists, conditional formatting, and data validation, make managing the cybersecurity planner both easy and efficient.
Best Practices for Using the Cybersecurity Planner Checklist
Implementing a Cybersecurity Planner Checklist can be even more effective when you follow these best practices:
-
Regular Updates: Cybersecurity threats evolve over time. Ensure that the checklist is updated regularly to reflect new security tasks, threats, and compliance requirements.
-
Prioritize Tasks: Some cybersecurity tasks are more critical than others. Prioritize them to address the most urgent vulnerabilities first. The checklist allows you to easily track which tasks are high-priority.
-
Ensure Clear Roles and Responsibilities: Assign specific tasks to individuals or teams and set clear deadlines. This ensures that everyone knows their role and there’s no ambiguity about who is responsible for what.
-
Leverage Excel’s Features: Use Excel’s data validation, dropdown lists, and conditional formatting features to make the planner more interactive and user-friendly. This will help reduce errors and improve the overall efficiency of the tool.
-
Monitor and Adjust: As tasks are completed, monitor progress and adjust the checklist as necessary. Use the progress bar and the counters to evaluate whether you are on track and adjust your approach if needed.
-
Ensure Backup and Security: While using an Excel template, always ensure that your file is backed up regularly, and access is restricted to authorized personnel only. A cybersecurity planner is only effective if the file itself is secure.
How to Use the Cybersecurity Planner Template in Excel
Using the Cybersecurity Planner Template in Excel is easy and straightforward. Follow these steps to get started:
-
Download the Template: First, obtain the Excel file containing the Cybersecurity Planner Checklist template. Open the file and review the structure.
-
Familiarize Yourself with the Layout: The template consists of two main sheets: the Cybersecurity Planner Checklist Sheet and the List Sheet. Familiarize yourself with these sheets and the columns provided.
Click to Purchases Cybersecurity Planner Checklist in Excel
Populate the Checklist Table:
- Add tasks to the Checklist Item column, describing what needs to be done.
- Fill in the Description and Remarks columns to provide more details.
- Assign responsible individuals in the Responsible Person column.
- Set deadlines for each task in the Deadline column.
- Use the Dropdown List: In the List Sheet tab, enter the names of all responsible individuals or teams. This will populate the dropdown list in the Responsible Person column, ensuring consistency and accuracy.
-
Track Progress: As tasks are completed, update the Status column to reflect whether the task has been finished (✔) or not (✘). The progress bar will automatically update based on the checked tasks.
-
Monitor and Adjust: Review the checklist periodically to ensure that all tasks are being completed on time. Make adjustments as needed to keep the cybersecurity measures up to date.
Conclusion
The Cybersecurity Planner Checklist in Excel is an invaluable tool for businesses looking to strengthen their security posture and reduce the risk of cyberattacks. By using a structured checklist, organizations can ensure that all tasks are tracked, completed on time, and assigned to the right people. The flexibility and ease of use offered by Excel make this template a great choice for managing cybersecurity tasks effectively.
Frequently Asked Questions (FAQs)
What is a Cybersecurity Planner Checklist?
A Cybersecurity Planner Checklist is a tool used to track and manage cybersecurity tasks and measures. It helps ensure that all essential cybersecurity actions are completed and monitored on time.
How do I use the Cybersecurity Planner Checklist Template in Excel?
To use the template, download the Excel file, fill in the checklist items, assign responsible persons, set deadlines, and track progress by updating the status of each task.
Can I customize the Cybersecurity Planner Checklist?
Yes, the template is fully customizable. You can add, modify, or remove checklist items, adjust columns, and tailor the template to fit your organization’s specific needs.
Why is it important to regularly update the Cybersecurity Planner Checklist?
Cybersecurity threats evolve rapidly, so it’s crucial to update the checklist regularly to stay ahead of new risks and compliance requirements. Regular updates ensure that your cybersecurity measures remain effective.
How do I track progress in the Cybersecurity Planner Checklist?
The checklist includes a progress bar and counters for Total Count, Checked Count, and Crossed Count, allowing you to monitor how many tasks have been completed and track your overall progress.
Visit our YouTube channel to learn step-by-step video tutorials