Cybersecurity has become a critical part of any organization’s strategy. With increasing threats from hackers and data breaches, it is essential for businesses to ensure their security measures are effective. A cybersecurity review checklist is one of the best ways to systematically evaluate security practices and maintain strong defenses against cyber threats.
In this article, we will introduce a Cybersecurity Review Checklist Template in Excel, designed to help businesses track and manage their cybersecurity practices efficiently.
Click to Purchases Cybersecurity Review Checklist in Excel
What is a Cybersecurity Review Checklist?
A Cybersecurity Review Checklist is a tool used to evaluate the effectiveness of an organization’s cybersecurity measures. It helps ensure that all security aspects are addressed, from risk management to data protection, and provides a systematic way of reviewing and improving cybersecurity protocols.
Key Features of the Cybersecurity Review Checklist Template in Excel
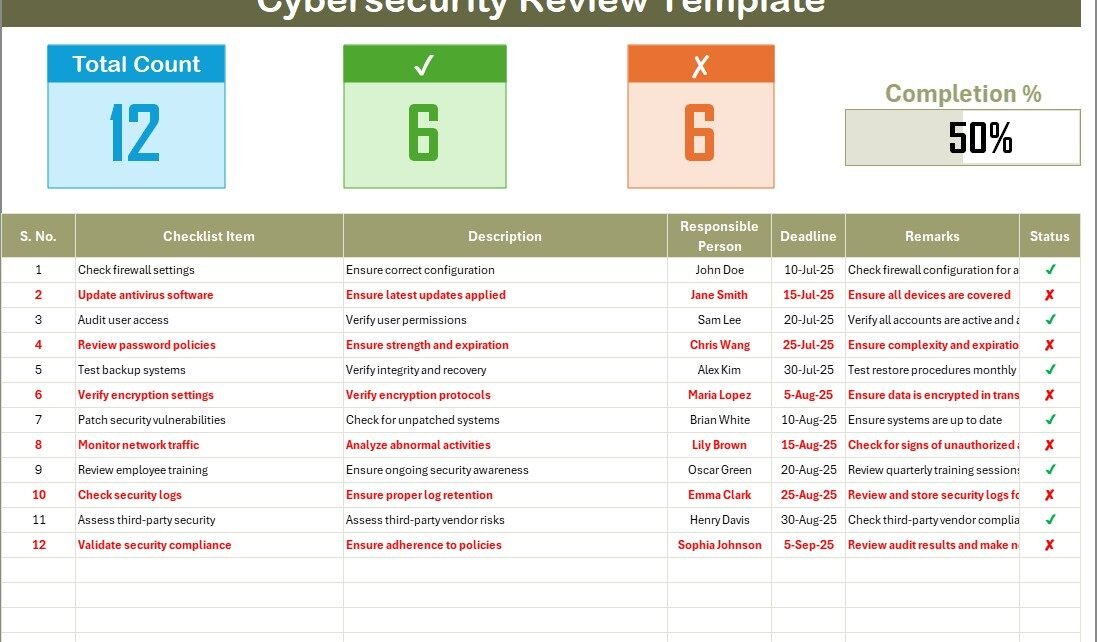
The Cybersecurity Review Checklist Template offers an organized way to track various cybersecurity-related activities. It consists of two primary sheets designed for ease of use and maximum effectiveness.
Cybersecurity Review Checklist Sheet

The main sheet is designed to capture all the essential information related to the cybersecurity review. Here’s what you can expect:
Top Section: This section provides a snapshot of your cybersecurity review status. It includes:
- Total Count: Displays the total number of items in the checklist.
- Checked Count: Shows the number of items marked as completed or reviewed.
- Crossed Count: Tracks the items that have been marked as completed and crossed off.
- Progress Bar: This visually represents the percentage of tasks completed, helping you track your progress at a glance.
Checklist Table: The checklist table is where you’ll input detailed information. It includes the following columns:
- Serial No.: Each item is numbered for easy reference.
- Checklist Item: Describes the specific action or task.
- Description: Provides additional details about the task.
- Responsible Person: Lists the person or department responsible for completing the task.
- Deadline: Specifies the deadline for task completion.
- Remarks: Offers space for additional notes or comments regarding the task.
- Status: Allows you to mark tasks as completed (✔) or incomplete (✘).
List Sheet Tab

This sheet is designed to streamline the task assignment process. It captures the unique list of responsible persons, which is then used to create a drop-down list in the main checklist sheet. This feature ensures consistency and simplifies assigning tasks, making it easier to manage cybersecurity reviews across different teams.
Advantages of Using a Cybersecurity Review Checklist in Excel
Using a cybersecurity review checklist offers several advantages to businesses looking to streamline their cybersecurity efforts:
1. Efficient Tracking and Management
The template allows businesses to track their cybersecurity activities in a structured manner. With the checklist format, you can ensure no aspect of cybersecurity is overlooked.
2. Ease of Use
Excel is a widely used tool, making it accessible to most businesses. The template requires no additional software, and its user-friendly interface makes it easy for teams to get started quickly.
3. Customizable
The template can be easily modified to fit your company’s specific needs. You can add new items to the checklist, adjust deadlines, and include additional comments or statuses as required.
4. Centralized Information
With all cybersecurity review data stored in one place, businesses can quickly assess their overall security posture and identify areas for improvement.
Best Practices for Using a Cybersecurity Review Checklist in Excel
To maximize the effectiveness of the Cybersecurity Review Checklist Template, here are some best practices to follow:
1. Regularly Update the Checklist
Cybersecurity is a constantly evolving field. Regularly updating the checklist ensures that new threats and vulnerabilities are addressed, keeping your security measures up to date.
2. Involve the Right People
Make sure the right individuals are assigned to the tasks. By using the responsible person list and assigning tasks based on expertise, you ensure that each task is handled by the most qualified person.
3. Set Realistic Deadlines
Ensure that deadlines are achievable to maintain motivation and productivity. Regularly review these deadlines to ensure they are still relevant.
4. Prioritize Critical Tasks
Not all tasks will carry the same level of urgency. Prioritize tasks that are vital to the overall security of your organization, such as patching vulnerabilities or conducting employee training.
5. Use the Progress Bar
Keep track of the progress of your cybersecurity review with the help of the progress bar. It provides a quick and visual representation of how much work has been completed and how much is left to do.
Frequently Asked Questions (FAQs)
1. What should be included in a cybersecurity review checklist?
A cybersecurity review checklist should cover various areas, including risk management, data protection, access control, network security, and incident response. Ensure that tasks are comprehensive and relevant to your organization’s specific needs.
2. Can I modify the Cybersecurity Review Checklist Template?
Yes, the Cybersecurity Review Checklist Template in Excel is fully customizable. You can add new items, adjust deadlines, and modify the drop-down lists to fit your company’s structure and specific needs.
3. How often should I perform a cybersecurity review?
The frequency of cybersecurity reviews depends on your organization’s risk exposure and industry requirements. It’s recommended to conduct reviews at least once a year, though more frequent assessments may be necessary in high-risk industries or after significant security incidents.
4. How do I track the progress of the cybersecurity review?
The template includes a progress bar that visually represents how much of the checklist has been completed. You can also track the number of checked and crossed items to assess progress.
5. What happens if a checklist item is not completed on time?
If a checklist item is not completed by the deadline, it’s essential to assess why the task was delayed. You can adjust deadlines or reassign tasks to ensure that critical cybersecurity measures are not overlooked.
Conclusion
In today’s digital world, cybersecurity is non-negotiable. A Cybersecurity Review Checklist helps you stay on top of your organization’s security protocols by ensuring that no crucial task is missed. The Cybersecurity Review Checklist Template in Excel provides an easy-to-use, customizable, and efficient tool for managing your cybersecurity reviews.
Visit our YouTube channel to learn step-by-step video tutorials