In today’s digital world, IT security is no longer optional—it is a necessity. Cyber threats are evolving at a rapid pace, and organizations of all sizes must adopt proactive measures to safeguard their systems, data, and employees. One of the most effective ways to stay organized and secure is by using an IT Security Planner Checklist in Excel.
This article will walk you through everything you need to know about this powerful tool. We will cover its features, benefits, use cases, best practices, and provide answers to the most common questions. By the end, you will have a clear understanding of how to implement and manage IT security effectively with this checklist.
What Is an IT Security Planner Checklist in Excel?
Click to Purchases IT Security Planner Checklist in Excel
An IT Security Planner Checklist in Excel is a structured, ready-to-use template designed to help organizations track, monitor, and execute security-related tasks. Instead of relying on scattered notes or ad-hoc processes, this checklist organizes all security activities in one place.
The Excel-based template allows businesses to:
-
Plan IT security activities.
-
Assign responsibilities to team members.
-
Monitor progress with real-time status tracking.
-
Maintain accountability across the organization.
Unlike static paper checklists, this template uses dynamic features such as progress bars, dropdown lists, and automated calculations to make security planning simple, efficient, and effective.
Key Features of the IT Security Planner Checklist
This checklist template comes with two main worksheet tabs, each serving a unique purpose:
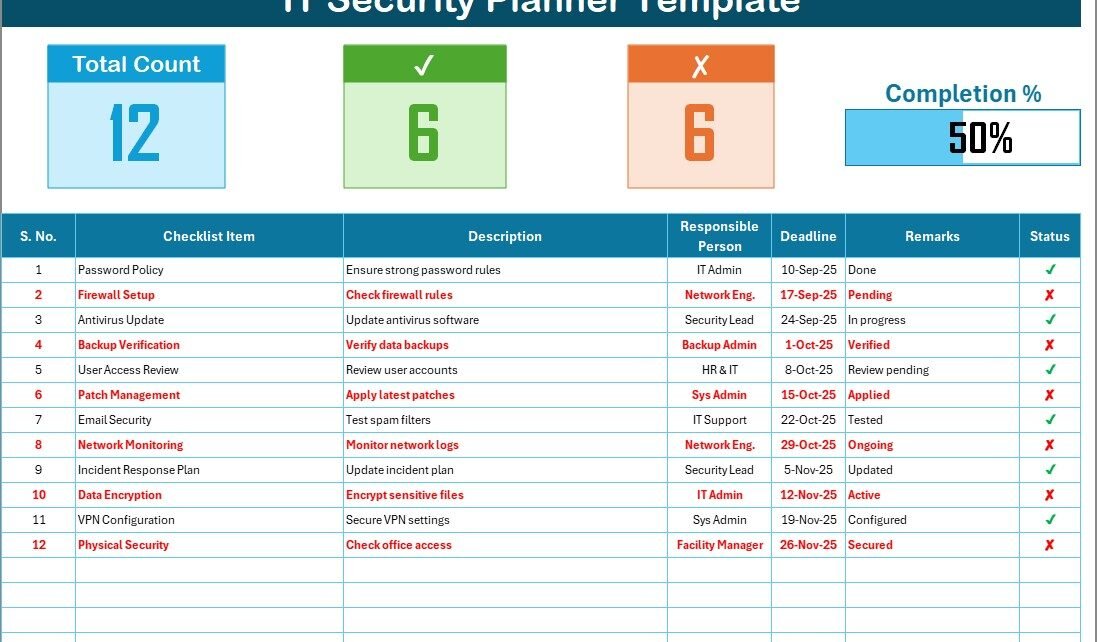
IT Security Planner Checklist Sheet Tab
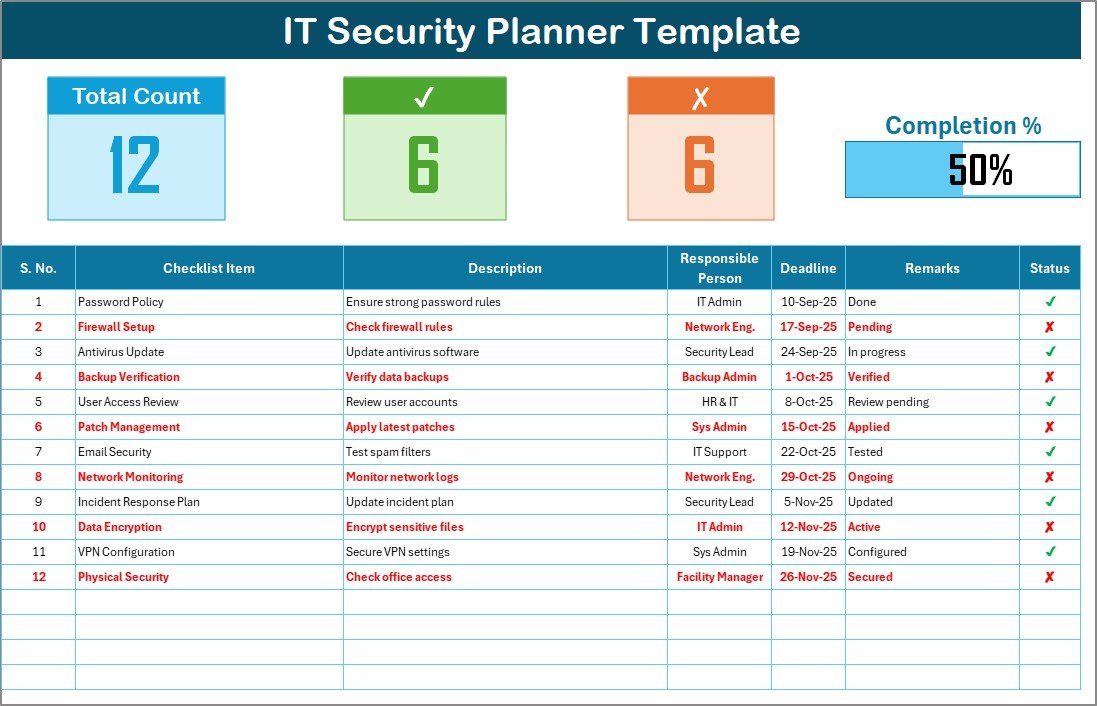
This is the main working sheet where all activities are tracked.
Top Section Overview
- Total count of security tasks.
- Number of completed (✔) and pending (✘) tasks.
- A progress bar showing the overall completion percentage.
Checklist Table
The structured table includes the following columns:
- Serial No. – Unique task ID for tracking.
- Checklist Item – The security measure or task.
- Description – Short explanation of the task.
- Responsible Person – Assigned team member.
- Deadline – Task due date.
- Remarks – Notes or comments.
- Status – Mark as ✔ (done) or ✘ (pending).
List Sheet Tab
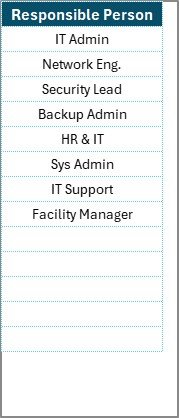
This sheet is used for managing a unique list of responsible persons. It ensures consistency by enabling dropdown lists in the main table. Instead of manually typing names, users can simply select from a predefined list, reducing errors and saving time.
Why Should Businesses Use an IT Security Planner Checklist?
Many organizations overlook structured security planning because they think their IT team can “handle it.” However, this approach often leads to missed steps and increased vulnerabilities. Here’s why you need this checklist:
-
Centralized Security Tracking – All security tasks in one place.
-
Clear Accountability – Each task is assigned to a responsible person.
-
Real-Time Monitoring – Progress is instantly visible with a progress bar.
-
Error Reduction – Dropdown lists prevent inconsistent data entry.
-
Scalability – Works for small startups and large enterprises alike.
Advantages of IT Security Planner Checklist in Excel
Implementing this checklist comes with a range of benefits:
✅ Improved Organization – Keep all IT security activities neatly structured.
✅ Better Collaboration – Teams can share responsibility and track progress.
✅ Time-Saving – Automated counts and progress indicators eliminate manual tracking.
✅ Flexibility – Customize columns, tasks, and deadlines to suit your business needs.
✅ Enhanced Security Posture – Regular monitoring ensures nothing falls through the cracks.
How to Use the IT Security Planner Checklist
Click to Purchases IT Security Planner Checklist in Excel
Using the template is straightforward. Here’s a step-by-step guide:
-
Download the Template – Open it in Excel.
-
Customize the Checklist Items – Add tasks relevant to your organization.
-
Assign Responsible Persons – Use the dropdown list for consistency.
-
Set Deadlines – Add realistic due dates for each activity.
-
Update Status – Mark ✔ when complete, ✘ when pending.
-
Monitor Progress – Track overall completion through the progress bar.
-
Review and Adjust – Regularly revisit tasks to keep the checklist updated.
Examples of Tasks in an IT Security Planner Checklist
Here are some typical IT security activities you might include:
-
Implement strong password policies.
-
Set up two-factor authentication.
-
Regularly back up company data.
-
Update firewalls and antivirus software.
-
Conduct phishing awareness training.
-
Review user access permissions.
-
Test disaster recovery procedures.
-
Encrypt sensitive files and databases.
-
Monitor network traffic for suspicious activity.
-
Audit third-party vendor security compliance.
Best Practices for the IT Security Planner Checklist
To maximize the effectiveness of your checklist, follow these best practices:
🔒 Keep It Updated – Cybersecurity threats evolve; update tasks regularly.
👥 Assign Clear Roles – Ensure accountability by assigning each task to a person.
📊 Use the Progress Bar – Monitor completion rates to avoid missed deadlines.
🗂️ Group Tasks by Category – Divide tasks into areas such as data protection, network security, and compliance.
🕒 Set Realistic Deadlines – Avoid overloading employees with tight schedules.
🔄 Review Periodically – Conduct monthly or quarterly reviews.
📑 Document Everything – Use remarks for notes, references, or audit trails.
🚨 Include Incident Response – Add steps for handling breaches or attacks.
Opportunities for Improvement
Even though the template is highly useful, you can enhance it further by:
-
Integrating with Power BI – Convert checklist data into interactive dashboards.
-
Automating Reminders – Use Excel VBA to send task deadline notifications.
-
Adding Risk Scoring – Assign risk levels to prioritize high-impact tasks.
-
Linking Policies and Documents – Attach references to policies for quick access.
Who Can Benefit from an IT Security Planner Checklist?
This template is versatile and can be used by:
-
Small Businesses – To build a foundation for IT security.
-
Large Enterprises – For structured, department-level monitoring.
-
IT Managers – To oversee compliance and readiness.
-
Auditors – To verify that security procedures are followed.
-
Consultants – To provide clients with organized security plans.
Conclusion
The IT Security Planner Checklist in Excel is more than just a document—it is a strategic tool that empowers organizations to strengthen their cybersecurity posture. With its dynamic features like progress bars, dropdown lists, and automated counts, it simplifies complex IT security planning into manageable steps.
By following best practices, keeping the checklist updated, and ensuring accountability, businesses can prevent vulnerabilities and stay one step ahead of cyber threats. In a world where data breaches can cause millions in losses, this tool provides a simple yet powerful way to ensure security readiness.
Frequently Asked Questions (FAQs)
1. What is an IT Security Planner Checklist in Excel?
It is a structured Excel template that helps organizations track IT security activities, assign responsibilities, and monitor progress with real-time indicators.
2. Can small businesses use this checklist?
Yes, it is flexible enough for small startups as well as large enterprises.
3. What kind of tasks should I include in the checklist?
Tasks like password policies, backups, access reviews, antivirus updates, incident response, and compliance checks are common.
4. How does the progress bar work?
The template calculates completed tasks (✔) and shows progress as a percentage, displayed visually in a progress bar.
5. Can I customize the checklist for my company?
Absolutely. You can add or remove checklist items, change deadlines, and edit responsible persons.
6. Is this template suitable for audits?
Yes, auditors can use it to verify compliance with IT security standards and regulations.
7. How often should I review the checklist?
At least monthly, though quarterly reviews are also effective depending on organizational needs.
8. Can the checklist send reminders automatically?
By default, Excel does not send reminders, but you can enhance the template with VBA macros to send alerts.
9. What makes this checklist better than a paper checklist?
It provides automation, dynamic progress tracking, dropdown lists, and scalability, which a paper checklist cannot offer.
10. Where can I get this template?
The template is available for download from professional template providers like NextGenTemplates.com and similar platforms.
Visit our YouTube channel to learn step-by-step video tutorials